An unnamed scientific researcher walks out to her mailbox, shuffles through some bills and advertisements, and pulls out an envelope containing a CD of pictures from a recent scientific conference the researcher had attended in Houston. Excited – though maybe a bit nervous – to see the candid photos of herself and her colleagues snapped by an excitable event photographer, the researcher walks inside, casually drops the unopened bills on the kitchen table, opens up her laptop, and slides in the CD. Windows asks if she’d like to open the pictures to view them. She accepts, and the pictures pop up in the photo viewer. One by one she clicks through them, viewing the photos from the event. She reminisces fondly, wincing only at that one photo where she looks either drunk or high, making mental note of the pictures to print out for her lab desk.
What the researcher doesn’t see, however, is a malicious payload – a virus, one of the most sophisticated known to man – secretly installing itself in the background of her computer. This virus would give a certain secret group of individuals complete access to her system, a group which had hijacked the package mid-transit in the mail, replaced the original CD with a copy that included the virus, taped everything back up without evidence of tampering, and sent the package on its way to her. The virus was practically untraceable and completely irremovable; it could map out networks, jump to computers not connected via the Internet, and even selectively target and destroy specific computers much like a bioengineered nano-virus – all at the direction of a secret shadow organization that was covertly infiltrating the world’s most secure computer systems.
The Equation Group
What may sound like the start to a Tom Clancy novel, or an episode of 24, is, in fact, completely real, the likes of which actually happened to one or more researchers back in 2009. In fact, surreptitious, interdiction-based cyberattacks like this one have apparently been happening since at least the early 2000s and may date back to 1996.
Last Monday, Moscow-based Kaspersky Lab released a cybersecurity report uncovering details about the most sophisticated, covert, and pervasive hacker groups known to man and possibly ever imagined. The organization, dubbed the Equation Group due to the group’s affinity towards sophisticated encryption methods, had operated practically undetected for over a decade, silently infecting computers across the globe and delivering attack payloads still unknown.
“There is nowhere I can’t go. There is nowhere I won’t find you.” – Bane, The Matrix Revolutions
Kaspersky Lab, a cybersecurity firm known primarily for its antivirus software, is no stranger to hackers. The company tracks and documents security breaches of all shapes and sizes.
For years, most high-profile computer hacks had been primarily the work of individuals or small groups motivated by curiosity or, more recently, financial interest – gray-collar criminals who would infiltrate computer systems for credit card numbers to sell on the black market. Usually these attacks are relatively unsophisticated, relying on bad operational cybersecurity practices (dubbed “opsec”) from corporations to create exploitable security holes like those seen in the recent Target and Home Depot security breaches. Only upon the discovery of the Stuxnet virus in June 2010 that sabotaged Iran’s Natanz uranium enrichment facilities have cybersecurity researchers and the public at large turned an eye towards advanced persistent threats (APTs) which use advanced hacking techniques capable of bypassing strong opsec protocols.
What make Equation Group so impressive are their “almost superhuman” technical feats, which include never-before-seen levels of ingenuity in hacking, engineering, and encryption. Those feats include:
- using virtual file systems like those found in the Regin (a.k.a. WarriorPride) malware attack used by the NSA to infect overseas computers;
- the ability to infect and surveil sensitive air-gapped (i.e. non-Internet connected) networks by piggybacking on USB flash drives, much like the Stuxnet virus;
- encrypting malicious files and storing them in multiple branches of the Windows registry, making it immune to detect with antivirus software;
- using over 300 Internet domains and 100 servers to command and control malware infrastructure; and
- hijacking URL requests on iPhones to spoofed Mac servers, which indicates that Equation Group has compromised the iOS and OSX operating systems.
Hollywood good
Perhaps most impressive is an Equation Group malware platform that rewrites the firmware of infected hard drives, allowing the virus to survive even low-level reformatting that is used to securely wipe a hard drive. All major hard drive manufacturers have drive models that have been compromised, including Western Digital, Seagate, Maxtor, Samsung, IBM, Toshiba, and Micron. Once the drive has been infected, the malware is completely impossible to detect or remove; the drive is compromised forever.
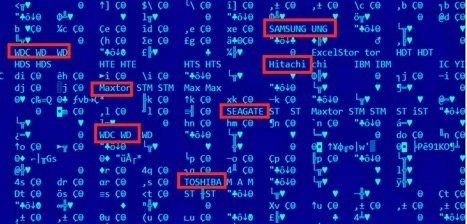
Forensics software displays, in Matrix-like fashion, some of the hard drives Equation Group was able to successfully hijack. (Credit: Kaspersky)
The difference in sophistication between your average Internet hacker and Equation Group cannot be understated. Your run-of-the-mill hacker is more or less equivalent to your run-of-the-mill burglar, who might break into a place with all of the sophistication of opening an unlocked door or busting out a window with a crowbar. APTs are more like museum thieves who might dress up like a guard or clone a keycard to snatch a valuable diamond or painting. Equation Group is an APT well beyond its peers, using super-spy tactics with analogical laser grids, vent shafts, and harnesses to swap a diamond with a perfect replica, remaining entirely undetected. It’s the stuff of Hollywood’s Mission: Impossible, only without the gratuitous explosions and Tom Cruise (…at least as far as anyone knows). And like Mission: Impossible, Equation Group is more than likely a clandestine operation of the U.S. government.
via RedOrbit