Dec 21, 2013 | Abuses of Power, Leaks, News
Hmm. Hold up. So if we go by this Wikipedia entry.. “Founded as an independent company in 1982, RSA Security, Inc. was acquired by EMC Corporation in 2006 for US$ 2.1 billion and operates as a division within EMC.[5]” People need to understand, this means...
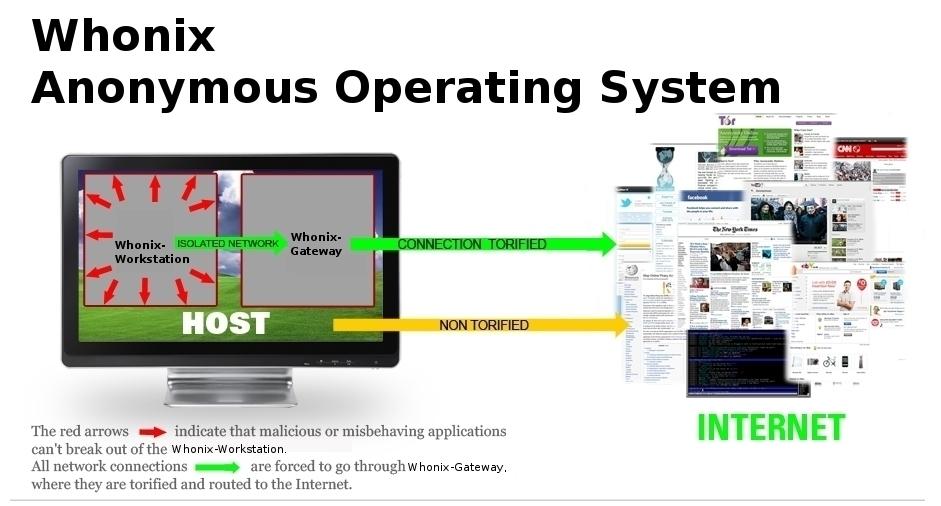
Oct 13, 2012 | Anonymous, Survivalism
Whonix is an anonymous general purpose operating system based on Virtual Box, Ubuntu GNU/Linux and Tor. By Whonix design, IP and DNS leaks are impossible. Not even malware with root rights can find out the user’s real IP/location. Whonix consists of two...

Oct 10, 2012 | Black Technology, Survivalism
Rejoice, paranoid security fanatics! There’s finally a version of Android that enables your obsessive need to lock and control each and every file on your mobile device. There’s just one catch: you’ve got to trust the National Security Agency to use it. The NSA has...

Sep 4, 2012 | Anonymous, News
Security professionals, geeks and hackers around the world are hosting a series of cryptography training sessions for the general public. The ‘crytoparty’ sessions were born in Australia and kicked off last week in Sydney and Canberra along with two in the...

Jul 12, 2012 | Abuses of Power, News
There was some surprise in the comments of yesterday’s post over the fact that the United Kingdom has effectively outlawed encryption: the UK will send its citizens to jail for up to five years if they cannot produce the key to an encrypted data set. First of all,...

May 10, 2012 | Abuses of Power, News
It has emerged that Michigan State Police have been using a high-tech mobile forensics device that can extract information from over 3,000 models of mobile phone, potentially grabbing all media content from your iPhone in under two minutes. The CelleBrite UFED is a...