Courtesy of Cryptome’s link distribution, we get a glimpse into the mind of 1952 (an era when crypto on land lines was very limited, indeed). We get to see how the US tapped and how it worked with the phone company to tap others – in the course of determining that standard US techniques for taps were not present (2-wire pair line tampering, inductive tapping of the 2-wire pair on local telephone pole, tapping of the “multiplying line” extensions).
Courtesy of Cryptome’s link distribution, we get a glimpse into the mind of 1952 (an era when crypto on land lines was very limited, indeed). We get to see how the US tapped and how it worked with the phone company to tap others – in the course of determining that standard US techniques for taps were not present (2-wire pair line tampering, inductive tapping of the 2-wire pair on local telephone pole, tapping of the “multiplying line” extensions).
Let’s not forget jus “how physical” was telephony, in 1952.
We also get to see the reaction to (activated) resonant cavity class of listening device – distinct from tapping lines.
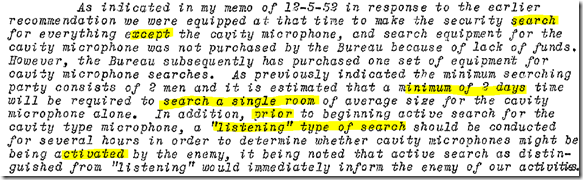
One sees the resource requirements, and the basic attack plan for the new threat (and the desire not to alert the tapper, presumably so the tap could be turned to dis-information).
One notes that searchers were familiar with microphony attacks in general, though not the cavity resonant devices initially.
Earlier disclosures show that the high level FBI agent had two classes of phone – those served by the phone company and those installed by DoD (obvious from the context of the redacted material). This shows that, in the 1950s, FBI was very much sub-servient to DoD in technical countermeasures.
At the same time, we note how the FBI was viewed as a go-to agency, by others (not that there is any suggestion that there is a law enforcement rationale to such requests).
The USPS (as a giant spying agency on paper) was probably one source, and one notes how the agencies were colluding to track EACH cabinet officer (of the government) for oral cues (as to the souce of leaks about USPS policies). This all seems consistent with the general state of red-scare paranoia of the period, as folks sought to address technical information leakage on the bomb, etc. Note that its all very much a pretext (to get the FBI into the “business”), since its all about the club of executives (not line sources).
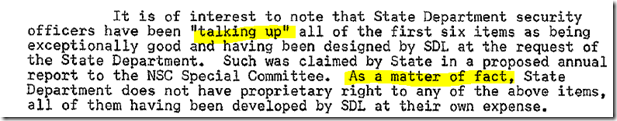
One sees also other civilian issues, including Bensons’ solid understanding of the price sensitivity (which seems a bit more coherent, and more tuned to issues of today):
Its fun to see the “most likely” sources of placement:
One sees some of the normal “art” of the searcher, used to American equipment:-
One notes a couple of references to the “countermeasure” device (which could be DoD/FBI trojan horse, of course):
An outline of its purposes follows (basically, it isolates the mic in the handset, or suppresses it own diaphragm)
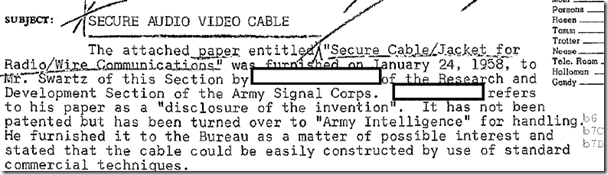
One sees a side threat, too, repurposing lines:
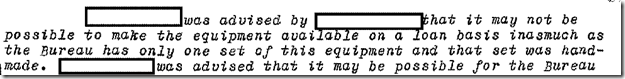
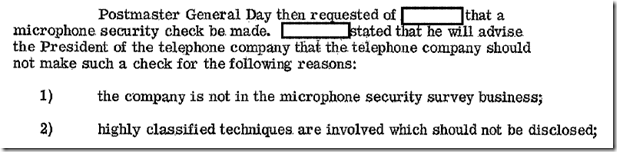
An interesting tit bit about the secret service wanting to do their own scan, and the FBI a sole source of the equipment (which was hand made, which is telling about FBI’s “Lab Division” technical capabilities in presumably valve electronics of the day).
At the same time, evidently there is a standard design (such that it can now be ”procured”).
One see several features of a general foil, since folks rationalize that its more important to protect the channel that to prevent leaks. They really WANT to use it for reverse signaling, consistent with 1945 counter-intelligence doctrine. There is also the assumption that the Presidents Office and Cabinet Office are really not secure areas (since the cabinet officers are necessarily surveilled proto-suspects, themselves).
One has to assume that non-FBI folks would also be testing FBI capabilities (since Hoover was such a known-deceiver). One sees how FBI is entirely compartmentalized from nuclear-level infosec/comsec (which must have irked Hoover no end).
One sees another reference to the infamous “British” equipment (which somewhat undermines the story about FBI being the sole-source of cavity mic detecting). Who operates the latter equipment is not disclosed.
we see a policy of information containment, concerning technical methods (including “acceptance” that white house could be a source of insecurity – national imperatives notwithstanding)
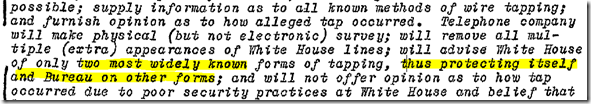
We see clearly how the FBI and the phone companies happily conspire to mis-inform and mid-direct the White house officials (in the hope that direct White House request be made of FBI, for an appropriate investigation, supported by technical means). It is more important to the FBI to protect this than protect the secrets being leaked!
One sees how Bell Labs is involved in subverting the signalling system, to aid tracing (suggesting that such tracing was not present, pre 1952). Having a secretary listen in to the call (and write it all up, soviet style, was deemed much more appropriate, as in White House conventions):
we also seem by 55, the emergence of ISIS, led by Treasury:
By 1955, one sees less scare about the cavity mic, and more action about compartmentalizing the Community buildings’s lines.
Folks are still obviously worried that the very proximity to the wire pairs afforded soviet tapping, of calls to friendly governments. One sees nothing about radio tapping though (where folks had the most skill.)
We also see some of the phone company responses emerging:
And, in other quotes we see the general attitude towards GSA, with phone companies wanting not to participate with GSA ‘infosec’ policies (preferring cosy relations with FBI, instead, with whom they have a working relation regarding authorized wire taps, anyways).
We see how transistors have made their mark (on size), by 1956:
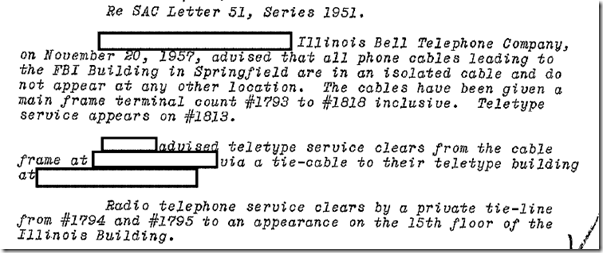
One sees s little of the architectural impact on the FBIs own buildings (with reference to tie lines, etc) and “mainframe” switching:
one sees countermeasure, in 1957, to (presumably) analogue signalling for video (though we recall, they had PCM in 1942. By 1957, did they have early codecs for video?)
we see a general fishing attempt against the c ontractors of state (where FBI has no jurisdiction) – seeking to perform an intelligence review:
We see the “former agent” network subverting agency policies, with “discreet checks”, being “caused”. Cooperating with such subversion seems not to be a worry for the FBI. even absent any rationale for an “investigation”. Its just normal to engage in this type of behaviour.
One sees an interesting fact about 1945:
One sees means used to isolate those who would be independent of the FBI’s technical expertise (in wire circuits, and sound recording):
one sees the mindset of the FBI, concerning microphony (and countermeasures):
All the drivel about inspecting handsets for “tampering” is a diversion, to the microphones outside the windows measuring the window’s reactance itself! There is a fair amount of policy-based deception going on.
When you look at the endless letters, one sees folks in “power” looking for assurance that someone makes them believe that a) their equipment is not being tampered with, and (b) they indeed have something worth keeping a secret (given how important, they now are).
one sees in a 1962 memo emergence of secure phone codecs (keyed by card), with attendant overhead of security officers responsible for the keying.
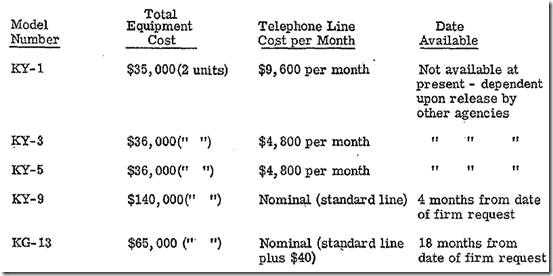
Interesting facts on capabilities, costs, leased line specificity and delay:
Someone helped the FBI out, on using window material to project sound:
Updating to 1981,
Updating to 1988, we see quite a marked change in the tone. There is a lot more professionalism on display, particularly once FBI formally ceded from DIA in handling the industrial security program. Upto 1995,