
Anonymous – The Bankers Are The Problem
Bankers Are the Problem – Greed has become the driving force of systematic DEBT in throughout the world

Bankers Are the Problem – Greed has become the driving force of systematic DEBT in throughout the world
Occupy Wall Street has called for a global day of action on October 15, and protesters are mobilizing all over the world. In the United States, the Occupy Wall Street movement has already spawned sizeable protests in New York, Washington DC, Boston, Seattle, San Francisco, Oakland, Austin, and other cities. Several of these movements have faced opposition from their local police departments, including mass arrests.
Protesters of all political persuasions are increasingly documenting their protests — and encounters with the police — using electronic devices like cameras and cell phones. The following tips apply to protesters in the United States who are concerned about protecting their electronic devices when questioned, detained, or arrested by police. These are general guidelines; individuals with specific concerns should talk to an attorney.
1. Protect your phone before you protest
Think carefully about what’s on your phone before bringing it to a protest. Your phone contains a wealth of private data, which can include your list of contacts, the people you have recently called, your text messages, photos and video, GPS location data, your web browsing history and passwords, and the contents of your social media accounts. We believe that the police are required to get a warrant to obtain this information, but the government sometimes asserts a right to search a phone incident to arrest — without a warrant. (And in some states, including California, courts have said this is OK.) To protect your rights, you may want to harden your existing phone against searches. You should also consider bringing a throwaway or alternate phone to the protest that does not contain sensitive data and which you would not mind losing or parting with for a while. If you have a lot of sensitive or personal information on your phone, the latter might be a better option.
Password-protect your phone – and consider encryption options. To ensure the password is effective, set the “password required” time to zero, and restart phone before you leave your house. Be aware that merely password-protecting or locking your phone is not an effective barrier to expert forensic analysis. Some phones also have encryption options. Whispercore is a full-disk encryption application for Android, and Blackberry also has encryption tools that might potentially be useful. Note that EFF has not tested these tools and does not endorse them, but they are worth checking into.
Back up the data on your phone. Once the police have your phone, you might not get it back for a while. Also, something could happen, whether intentional or not, to delete information on your phone. While we believe it would be improper for the police to delete your information, it may happen anyway.
2. You’re at the protest – now what?
Maintain control over your phone. That might mean keeping the phone on you at all times, or handing it over to a trusted friend if you are engaging in action that you think might lead to your arrest.
Consider taking pictures and video. Just knowing that there are cameras watching can be enough to discourage police misconduct during a protest. EFF believes that you have the First Amendment right to document public protests, including police action. However, please understand that the police may disagree, citing various local and state laws. If you plan to record audio, you should review the Reporter’s Committee for Freedom of the Press helpful guide Can We Tape?.
3. Help! Help! I’m being arrested
Remember that you have a right to remain silent — about your phone and anything else. If questioned by police, you can politely but firmly ask to speak to your attorney.
If the police ask to see your phone, you can tell them you do not consent to the search of your device. They might still legally be able to search your phone without a warrant when they arrest you, but at least it’s clear that you did not give them permission to do so.
If the police ask for the password to your electronic device, you can politely refuse to provide it and ask to speak to your lawyer. Every arrest situation is different, and you will need an attorney to help you sort through your particular circumstance. Note that just because the police cannot compel you to give up your password, that doesn’t mean that they can’t pressure you. The police may detain you and you may go to jail rather than being immediately released if they think you’re refusing to be cooperative. You will need to decide whether to comply.
4. The police have my phone, how do I get it back?
If your phone or electronic device was illegally seized, and is not promptly returned when you are released, you can file a motion with the court to have your property returned. If the police believe that evidence of a crime was found on your electronic device, including in your photos or videos, the police can keep it as evidence. They may also attempt to make you forfeit your electronic device, but you can challenge that in court.
Cell phone and other electronic devices are an essential component of 21st century protests. Whether at Occupy Wall Street or elsewhere, all Americans can and should exercise their First Amendment right to free speech and assembly, while intelligently managing the risks to their property and privacy.
LONDON (The Blaze/AP) — A group of computer hackers claims to have breached NATO security and accessed hordes of restricted material.
 The group called Anonymous says it would be “irresponsible” to publish most of the material it stole from NATO but that it is sitting on about 1 gigabyte of data.
The group called Anonymous says it would be “irresponsible” to publish most of the material it stole from NATO but that it is sitting on about 1 gigabyte of data.
Anonymous posted a PDF file Thursday on its Twitter page showing what appeared to be a document headed “NATO Restricted:”
Anonymous is a loosely organized group of hackers sympathetic to WikiLeaks. It has claimed responsibility for attacks against corporate and government websites worldwide.
The group also claims credit for disrupting the websites of Visa and MasterCard in December when the credit card companies stopped processing donations to WikiLeaks and its founder, Julian Assange.
The reported hack comes on the heels of cyber security arrests made Tuesday. Fourteen people were taken into custody for allegedly mounting a cyberattack on the website of PayPal in retaliation for its suspending the accounts of WikiLeaks as part of the hacker group LulzSec.
Separately, FBI agents executed more than 35 search warrants around the country in an ongoing investigation into coordinated cyberattacks against major companies and organizations.
As part of the effort, there were two arrests in the United States unrelated to the attack on the PayPal payment service. Overseas, one person was arrested by Scotland Yard in Britain, and there were four arrests by the Dutch National Police Agency, all for alleged cybercrimes.
Could it be that this is in part retaliation? Maybe. The group also sent out a joint tweet with LulzSec giving a statement to the FBI:
 The statement is bold. It says the FBI will not be able to stop the groups, and lays out complaints both have against the government:
The statement is bold. It says the FBI will not be able to stop the groups, and lays out complaints both have against the government:
It seems Anonymous reads The Blaze, too:
Anonymous is on the hunt for the cop featured in a videopepper-spraying Occupy Wall Street protesters for no apparent reason. They say they’ve found him, and are circulating a document with his and his family’s personal information. This could get ugly.
According to a document posted on Pastebin.com, the cop who blasted young women in the face with pepper spray in the now-iconic video above is NYPD Captain Deputy Inspector Anthony Bologna. Bologna was identified as the pepper-sprayer by a photographer who witnessed the incident and posted a blown-up image of his badge to his blog.
The Pastebin document, which has about 7,000 views at this writing contains Bologna’s name and possible phone numbers and addresses, along with a list of potential family member names. It reads:
You know who the innocent women were, now they will have the chance to know who you are. Before you commit atrocities against innocent people, think twice. WE ARE WATCHING!!! Expect Us!
According to a 2005 article in the Villager, Anthony Bologna has been with the NYPD for nearly 30 years. He was in charge of Lower Manhattan’s police precinct for five years, before becoming the “borough executive” of the Manhattan South Precinct in 2010.
What might Anonymous do with this information? One popular Anonymous twitter account asked: “Question: what kind of pizza do you think Antony Bologna would like?”—a reference to the group’s favored harassment tactic of sending a flood of pizzas to victims’ houses. If Bologna has any nude pics floating around he might want to clean those up, as Anonymous leaked nude pics of a BART spokesman during protests of San Francisco’s public transit police.
NYPD, which told the New York Times pepper spray was deployed “appropriately,” did not immediately return a request for comment.
Cyber activists associated with Anonymous have been in the forefront of helping to organize and conduct protests against Wall Street bankers in New York City.
Rallying under the banner of #OCCUPYWALLSTREET, the demonstrators say they want to change America’s financial system for the better.
For example, Bill Steyerd, a Vietnam veteran from Queens, told The Guardian that #OCCUPYWALLSTREET is a “worthy cause because people on Wall Street are blood-sucking warmongers.”
Jason Ahmadi, who travelled from Oakland, California to attend the rally, said “a lot of us feel there is a large crisis in our economy and a lot of it is caused by the folks who do business here.”
Meanwhile, Robert Siegel, who is sleeping in a nearby park during the protest, told WCBS that working 8 years as a consultant for an investment bank was enough to turn him against the current Wall Street model.
“I just shuffled other people’s money around and took a cut. Nothing was being contributed. A lot was just being taken out.
”[I] watched the silliness compound on itself. At some point, I wanted a lifestyle that didn’t consist of going up to computers to deal with angry people.”
http://www.tgdaily.com/business-and-law-features/58550-anonymous-helps-lead-wall-street-protests
In Friday’s Washington Post, Greg Miller and Julie Tate published a must-read study tracing the evolution of the Central Intelligence Agency from an intelligence-collection and -analysis operation into a shadow military force:
In the decade since the Sept. 11, 2001, attacks, the agency has undergone a fundamental transformation. Although the CIA continues to gather intelligence and furnish analysis on a vast array of subjects, its focus and resources are increasingly centered on the cold counterterrorism objective of finding targets to capture or kill.
At the core of this evolution, we discover, is that for the first time in its history, the CIA has secured control of a state-of-the-art weapons system:
The drone program has killed more than 2,000 militants and civilians since 2001, a staggering figure for an agency that has a long history of supporting proxy forces in bloody conflicts but rarely pulled the trigger on its own.
Miller and Tate note that the agency’s Counterterrorism Center, which controls the drone fleet, now has 2,000 staffers, outnumbering current estimates of Al Qaeda’s membership.
Though the authors focus on the CIA’s new drone operation in the Arabian Peninsula, the Agency is also managing the war effort on the Pakistan side of the Durand Line separating that country from Afghanistan, which the Obama Administration made clear from the outset would be the central theater of its military campaign. The CIA’s mission there is plain: not simply to collect intelligence on a hostile military force, but to target and eliminate it.
Such efforts have nothing to do with the CIA that was born under the National Security Act of 1947. The Agency has adopted responsibilities that were formerly the preserve of the uniformed military. As the ACLU’s Hina Shamsi told Miller and Tate, “We’re seeing the CIA turn into more of a paramilitary organization without the oversight and accountability that we traditionally expect of the military.”
To add to Shamsi’s critique: The American military is trained to operate under the laws of armed conflict. It has professional officers sworn to ensure adherence to those laws, and a Uniform Code of Military Justice that provides a tool for enforcement. The CIA has no such checks. In fact, its culture has for decades been built on the notion that it operates outside of the laws of war.
The Agency’s transformation points to changes in the inner dynamics of the American national security establishment and its relationship to government. Institutions grow out of their initial boundaries and assume previously forbidden functions via a process of aggressive self-assertion. Such shifts — and the hundred-billion-dollar commitments of public resources that they entail — were once subject to public discussion and congressional deliberation. Not so in the unconstrained national-security state that is one of the most deeply entrenched legacies of 9/11.

A Primer on Wikileaks Espionage on Tor Exit Nodes

Note* Anon walks us through the bluster, and demonstrates just how Assange and Wikileaks compromised the TOR network. (AT)
In 2007, Dan Egerstad, Swedish security researcher, exposed how the
Tor network could easily be used for intelligence gathering: [1]
“Dan Egerstad is a Swedish security researcher; he ran five Tor
nodes. Last month, he posted a list of 100 e-mail credentials —
server IP addresses, e-mail accounts and the corresponding
passwords — for embassies and government ministries around the
globe, all obtained by sniffing exit traffic for usernames and
passwords of e-mail servers.”
Note that this was not a case of embassy staff using Tor to access
their own email accounts, which is absurd. This was a case of
blackhat hackers (or intelligence) using Tor to anonymously access
the compromised accounts. In fact, Egerstad states that the Iranian
government contacted him to thank him for having uncovered the
otherwise unknown compromise.
Also in 2007, a group of Canadian security researchers uncovered
`GhostNet,’ a vast spy network targetting Taiwanese, Vietnamese, and
American political figures, among others — including most notably
the Dalai Lama: [2][3]
“A vast electronic spying operation has infiltrated computers and
has stolen documents from hundreds of government and private
offices around the world, including those of the Dalai Lama,
Canadian researchers have concluded.”
China is strongly suspected of being behind GhostNet. [4] It’s
important to note the method by which the researchers were able to
uncover GhostNet: by monitoring the traffic of networks where data
was being exfiltrated — an unprecedented “electronic spy game.”
The researchers have not publicly stated which networks were being
monitored, but Egerstad and Kim Zetter of Wired magazine both
conclude that it was most likely Tor. [5]
In both these cases — that of lone researcher Egerstad, and that of
the University of Toronto research group — information was being
exfiltrated from compromised networks by hackers. The exfiltration
was then uncovered via network monitoring, aka `sniffing.’ In other
words, whitehat spies spied on blackhat spies.
In fact, Tor was admitedly designed for intelligence gathering
purposes by the Information Technology Division of the Naval
Research Laboratory of the United States Navy: [6]
“The purpose was for DoD / Intelligence usage (open source
intelligence gathering, covering of forward deployed assets,
whatever).”
But what does all this have to do with Wikileaks?
In January 2007, in a message sent to the then-secret Wikileaks
internal mailing list, Assange stated: [7]
“Hackers monitor chinese and other intel as they burrow into their
targets, when they pull, so do we. […] We have all of pre 2005
afghanistan. Almost all of india fed. Half a dozen foreign
ministries. […] We’re drowing. We don’t even know a tenth of
what we have or who it belongs to. We stopped storing it at 1Tb.”
What does “pull” mean, exactly? Who are these Chinese intelligence
sources, and how are “hackers” monitoring them? And what does
Assange mean by “when they pull, so do we?”
Given the trend documented above — i.e. whitehat spies spying on
blackhat spies — it is clear that “pull” refers to (Chinese)
blackhat exfiltration of data from compromised networks; and the
“so do we” refers to Wikileaks monitoring those exfiltration paths
(likely the Tor network) for any passing documents. In other words,
it could be construed that Wikileaks’ initial trove of documents were
not obtained from whistleblowers, but from spying on spies who were
using the Tor network to stay anonymous. This accusation has, indeed,
been leveled against the organization. [8] But is this really the
correct conclusion? Could it be a misunderstanding?
Consider the June 2010 profile on Assange and Wikileaks in The New
Yorker by Raffi Khatchadourian: [9]
“Before launching the site, Assange needed to show potential
contributors that it was viable. One of the WikiLeaks activists
owned a server that was being used as a node for the Tor network.
Millions of secret transmissions passed through it. The activist
noticed that hackers from China were using the network to gather
foreign governments’ information, and began to record this
traffic. Only a small fraction has ever been posted on WikiLeaks,
but the initial tranche served as the site’s foundation, and
Assange was able to say, `We have received over one million
documents from thirteen countries.’ ”
This seems to corroborate the statement by Assange on the Wikileaks
mailing list in 2007. However, could it have been a misquote? In June
2010, John Leyden of The Register begged Assange to clarify. [10]
Assange did not deny the statement he made to the Wikileaks mailing
list in 2007, nor the facts in The New Yorker article, only calling
the latter “misleading:”
“The imputation is incorrect. The facts concern a 2006
investigation into Chinese espionage one of our contacts were
involved in. Somewhere between none and handful of those
documents were ever released on WikiLeaks.”
That is, Assange dadmits a “handful” of documents obtained by
sniffing the Tor network were published by Wikileaks. What Assange
labels misleading is not the fact that Wikileaks published material
sniffed from the Tor network, but that Wikileaks was directly
involved in the espionage.
In sum, we have three distinct instances where Assange himself admits
that material obtained via espionage (sniffing the Tor network) was
published to Wikileaks. When pressed further, Assange replies —
“Get a life.” [11] — brushing aside the fact that the vast
majority of people, including his supporters, see serious ethical
issues in this type of behaviour. [12] In January 2011, an American
private security firm, Tiversa, stated that it had evidence that
Wikileaks had published sensitive documents obtained via espionage
on peer-to-peer networks. [13] The accusation is not new, nor unique.
Unfortunately, from all evidence, it seems espionage is the modus
operandi for Wikileaks.
[1] http://www.schneier.com/blog/archives/2 … d_t_1.html
[2] http://www.nytimes.com/2009/03/29/technology/29spy.html
[3] http://www.f-secure.com/weblog/archives/00001637.html
[4] http://news.bbc.co.uk/2/hi/7970471.stm
[5] http://www.wired.com/threatlevel/2009/0 … stem-focu/
[6] http://cryptome.org/0003/tor-spy.htm
[7] http://cryptome.org/wikileaks/wikileaks-leak2.htm
[8] http://www.wired.com/threatlevel/2010/0 … documents/
[9] http://www.newyorker.com/reporting/2010 … ntPage=all
[10] http://www.theregister.co.uk/2010/06/02 … ng_denial/
[11] http://motherjones.com/mojo/2010/06/wik … new-yorker
[12] http://ryansholin.com/2010/05/31/wikile … al-system/
[13] http://www.bloomberg.com/news/2011-01-2 … -data.html
LOS ANGELES—A member of the LulzSec hacking group was arrested this morning for his role in an extensive computer attack against the computer systems of Sony Pictures Entertainment, announced André Birotte Jr., the United States Attorney in Los Angeles; and Steven Martinez, Assistant Director in Charge of the FBI’s Los Angeles Field Office.
Cody Kretsinger, 23, of Phoenix, Arizona, was arrested this morning by FBI agents without incident. On September 2, 2011, a federal grand jury returned an indictment filed under seal in U.S. District Court in Los Angeles charging Kretsinger with conspiracy and the unauthorized impairment of a protected computer. The federal indictment was unsealed this morning upon Kretsinger’s arrest.
From approximately May 27, 2011, through June 2, 2011, the computer systems of Sony Pictures Entertainment were compromised by a group known as “LulzSec,” or “Lulz Security,” whose members anonymously claimed responsibility on LulzSec’s website. Kretsinger, also known by the moniker “recursion,” is believed to be a current or former member of LulzSec. The extent of damage caused by the compromise at Sony Pictures is under investigation.
According to the indictment, Kretsinger resided in Tempe, Arizona at the time the alleged criminal activity took place. In order to carry out the attack, Kretsinger allegedly sed a proxy server in an attempt to mask or hide his Internet Protocol (IP) address. The indictment alleges that Kretsinger and other coconspirators obtained confidential information from Sony Pictures’ computer systems using an “SQL injection” attack against its website, a technique commonly used by hackers to exploit vulnerabilities and steal information.
The indictment alleges that Kretsinger and his co-conspirators distributed the stolen information, including by posting the information on LulzSec’s website, and then announced the attack via its Twitter account. The indictment further alleges that, in order to avoid detection by law enforcement, Kretsinger permanently erased the hard drive of the computer he used to conduct the attack on Sony Pictures.
LulzSec is known for its affiliation with the international group of hackers known as “Anonymous.” Anonymous, according to the indictment, is a collective of computer hackers and other individuals located throughout the world that conduct cyber attacks, including the dissemination of confidential information stolen from victims’ computers, against individuals and entities they perceive to be hostile to its interests.
In the recent past, LulzSec has been linked to the hacking or attempted hacking of numerous targets, including various websites that represent governmental or business entities, among others.
Kretsinger will make an initial appearance before a federal magistrate in U.S. District Court in Phoenix today. The government will request that Kretsinger be removed to Los Angeles, the district in which he was charged, to face prosecution. If convicted, Kretsinger faces a statutory maximum sentence of 15 years in prison. This investigation was conducted by the Electronic Crimes Task Force (ECTF) in Los Angeles. The ECTF is comprised of agents and officers from the FBI, United States Secret Service, Los Angeles Police Department, Los Angeles County Sheriff’s Department, United States Attorney’s Office, Los Angeles County District Attorney’s Office, and the California Highway Patrol.
This case is being prosecuted by the United States Attorney’s Office in Los Angeles.
An indictment merely contains allegations that a defendant has committed a crime. Every defendant is presumed innocent unless and until proven guilty at trial.
Media Contact:
FBI Media Relations: 310 996-3343

 “Why I Hate Android”
“Why I Hate Android”
Why do I hate Android? It’s definitely one of the questions I get asked most often these days. And most of those that don’t ask probably assume it’s because I’m an iPhone guy. People see negative take after negative take about the operating system and label me as “unreasonable” or “biased” or worse.
I should probably explain.
Believe it or not, I actually don’t hate Android. That is to say, I don’t hate the concept of Android — in fact, at one point, I loved it. What I hate is what Android has become. And more specifically, what Google has done with Android.
Let’s turn back the clock. In 2006, the mobile landscape in the United States was almost unfathomably shitty. Motorola’s RAZR had been the top-selling device for something ridiculous like five straight years — and the only thing that didn’t suck about it was its physical size. The carriers completely controlled the industry. This cannot be overstated.
Then on January 9, 2007 — exactly 5 years ago today — Steve Jobs took the stage at Macworld to unveil the iPhone. Six months later it was released. While some laughed it off at the time, the mobile landscape completely changed.
Apple and Google were great allies at the time. They united over a common enemy: Microsoft. Then-Google CEO Eric Schmidt was even on Apple’s board of directors. Google was a huge part of original iPhone OS (before it was called iOS): Google Maps, YouTube, Google Search, etc. Apple could have launched the iPhone without Google, but it wouldn’t have been as good. And if they had to do something like build their own maps from scratch, it would have taken longer.
A few months later, on November 5, 2007, Google teamed up with many of the big players in the mobile/telecom space to announce the Open Handset Alliance. At the time it sounded promising, but perhaps it should have been the first warning sign. The first product of this partnership: Android. A beta was released, but it would take almost another year before the software was actually ready to go.
The initial Android prototypes looked a lot like BlackBerry devices (both in hardware and software). But the first device (the G1) and OS actually released was more of a cross between a T-Mobile Sidekick (which Android head Andy Rubin helped create while still a co-founder at Danger) and the iPhone OS.
In hindsight, Steve Jobs was clearly not happy about this and the subsequent iPhone-ification of Android. But great artists steal, etc, etc. The only thing I didn’t like about Android at the time was that it was a shitty copy of the iPhone. It was something you couldn’t pay me to use. And most people seemed to feel the same way.
Jobs probably didn’t say much at the time because he didn’t have to. The market was saying it.
Time went on and it was pretty clear that despite the major players involved in the OHA, Android wasn’t getting a lot of traction. Meanwhile, the iPhone, after a price-cut and addition of 3G technology, was soaring. So Google did the logical thing, they went to see Verizon, the largest U.S. carrier, and struck a deal.
Remember, Apple still had an agreement with AT&T for exclusive iPhone rights in the U.S. at the time. Verizon and Google needed each other. But Google clearly needed Verizon more. This was the first real problem. A deal with the devil was struck.
Let’s back up for a second.
Even before Android’s launch, Google clearly had big dreams for the mobile space. “Your mobile phone should be free,” Eric Schmidt told Reuters in late 2006. He envisioned a world in which consumers didn’t have to pay for their mobile phones — advertising (served by Google, naturally) would subsidize the cost. And we’re not talking “free” with a two-year carrier contract. We’re talking free free.
In the pre-iPhone world this may have sounded like crazy-talk. But remember, as an Apple board member and having purchased Android for Google in 2005, Schmidt knew what was coming down the pipe. He absolutely intended to disrupt the mobile market.
But again, the initial releases of Android simply didn’t have the traction needed to come close to fulfilling Schmidt’s (and Google’s) dream. So deals with the carriers had to be made.
Still, Google hung on to the hope of a free phone. That phone was called the Nexus One.
At an event in January of 2010, Google unveiled their plan for Nexus One — the first real “Google Phone” as it were. While they were cautious and cagey with some details, the goal seemed clear: Google intended to blow up the carrier market (in the U.S. first) by moving phone distribution online, flattening it in the process. The idea was that you’d go to a website and pick the phone you wanted, then pick the carrier you wanted, pay, and you’d be done.
Think about this for a second. Instead of going to the store of a single carrier and having a dozen shitty phones shoved in your face by salespeople that made commission, you’d be in total control of the process. The end result of consumers getting to choose their carriers (and phones and plans) was clear: major competition and subsequently a rush of better deals from said carriers to ensure customer activation and retention.
Or, you could buy whatever phone you wanted unlocked. Eventually, pay-as-you-go SIM cards would pop up in the U.S. as a result.
This was to be the dawn of the golden age of mobile in this country. As I wrote at the time: Apple And Google Just Tag Teamed The U.S. Carriers. I loved it.
But it was never meant to be.
What should have been obvious at the time but for whatever reason wasn’t (maybe because carrier representatives were at the event), the carriers hated this plan. And for good reason — it was going to turn them into dumb pipes that competed on price. There was no way they were going to let this fly, and they didn’t. Within a few months, citing weak sales of the Nexus One, Google scrapped their ambitious website and instead got fully in bed with the carriers.
But there was more.
What no one knew at the time, and I only heard months later, was Google’s original vision for the Nexus One. Google intended to sell it for $99 without a contract and unlocked. Yes, a $99 unlocked phone, subsidized by Google ads.
But the plan had one little problem: Google didn’t operate their own cellular network. They needed Verizon or AT&T or Sprint or T-Mobile to help them out. Google probably thought their open spectrum deal “win” in early 2008 gave them the leverage they needed here. Sadly, it did not.
All of the carriers laughed in Google’s face when presented with the ambitious Nexus One plan. And given that Google had just signed the all-important deal with Verizon, it was never going to happen.
So instead, at the Nexus One launch we got a website where you could indeed buy an unlocked Android phone — for $529. Nonstarter.
Better yet, while they said they were committed at the time, Verizon and Sprint never even got around to supporting the Nexus One at all. That’s how much they were behind the project.
To complicate matters further, behind the scenes, Verizon and Google were arguing over Net Neutrality rules. Verizon was opposed, Google was in favor. Then a funny thing happened. Google started supporting Verizon’s viewpoint on the matter! If you’re looking for the first post where I’m really, truly, pissed off at Google, look no further.
It. Was. Total. Fucking. Bullshit.
A few months later, guess what happened? Thanks to the Google/Verizon alliance on the matter, the FCC decided the compromised vision of Net Neutrality was just fine also. To be clear: Net Neutrality was thrown out in the wireless space because Google sided with Verizon’s ridiculous and horribly conflicted stance on the matter.
The open spectrum enemy, turned Net Neutrality enemy, became Google’s bedmate thanks to a business deal. Straight up. Greed, for lack of a better word, is good.
We got all of this thanks to Google’s desire for Android to take over the world. I commented earlier that they signed a deal with the devil — I wasn’t being facetious. They actually did! And they got away with it!
I think about these things everyday that I see positive news about Android. It’s so wonderful that the platform which helped cripple Net Neutrality and is keeping the evil carriers in control is taking off. Make no mistake: Android is now the carriers’ best friend.
Because Google sloppily decided to do the Motorola deal (driven by the full-on patent war, for which Apple and Microsoft, and not Google, are largely to blame), and because the model isn’t great for all but the biggest player, now the OEMs may be our best hope against the carrier/Android alliance.
Eventually, many of them will try to do their own thing (perhaps even using Android as a base) because they’re not idiots, they see where the real money is: controlling the entire experience. Like Apple.
All of this backstory knowledge fuels my rage. When I see Google talk about how “open” the platform is, setting it up as the foil to the “closed” (and framed as “evil”) iPhone, I want to scream and rip someone’s head off. It’s not only the most extreme example of being disingenuous that I can ever recall seeing — it’s nuclear bullshit.
Apple, for all the shit they get for being “closed” and “evil”, has actually done far more to wrestle control back from the carriers and put it into the hands of consumers. Google set off to help in this goal, then stabbed us all in the back and went the complete other way, to the side of the carriers. And because they smiled the entire time they were doing it and fed us this “open” bullshit, we thanked them for it. We’re still thanking them for it!
When you think about it in the context of this election season we’re entering, it’s a brilliant political maneuver that Google has pulled off with Android. They’ve taken something they’ve done that’s actually bad for us and spun it in such a way that most people actually buy into it being good for us.
And for the carriers, Android is the best thing ever because it’s the new “opiate for the masses”. Everything shitty they’re doing is great because they’re doing it with Android — at least it’s not iOS. What a load of horseshit.
I realize that the Android team at Google has a lot of good people doing great work. I know some of them. I respect them. But I cannot respect their decision to continue to work on this platform that perpetuates our imprisonment. I have to believe most simply chose not to think about these things. But they should. They really should.
There’s no denying that there are upsides to open — a lot of them. But in the case of Android, “open” has been hijacked and wildly contorted so as to mask the shady side of what’s really been going on. And it’s working.
So that, ladies and gentleman, is why I hate Android. It has nothing to do with the actual product (which continues to improve every year and is quite good now). It has to do with a promise that was broken and swept under the rug.
As crazy as it may sound to some of you, beyond a full OEM revolt (which could ultimately benefit the carriers as well), our hope now lies with Apple and Microsoft.
Apple, because they put the consumer first and have proven time and time again that they will not bend to carrier bullshit and will often work against them behind the scenes. And they control the all-important Apple stores for distribution (and, of course, the App Store).
Microsoft, because they have a model (many handsets on all carriers) that can potentially scale better than Apple’s can while still giving control (mostly) to the users. And they have Nokia on board with their plan. And they have intersections with products like Xbox. (Though it may be too late in the U.S.)
Perhaps more people will relate to this: I hate Android for the same reason that Severus Snape hates Harry Potter — the very sight reminds me of something so beautiful, that was taken. Except it’s worse. It’s as if Harry Potter has grown up to become Voldemort.

 The number of interested parties eager to listen in on your online conversations, including what you type through instant messaging, has never been higher.
The number of interested parties eager to listen in on your online conversations, including what you type through instant messaging, has never been higher.
It’s trivial to monitor unencrypted wireless networks and snatch IM passwords as they flow through the ether. Broadband providers and their business partners are enthusiastically peeking into their customers’ conversations. A bipartisan majority in Congress has handed the FBI and shadowy government agencies greater surveillance authority than ever before.
The need, in other words, for secure IM communication has never been greater. But not all IM networks offer the same privacy and security. To chart the differences, CNET News.com surveyed companies providing popular IM services and asked them to answer the same 10 questions.
One focus was how secure the IM service was–in other words, does it protect users against eavesdropping? It’s been 12 years since the introduction of ICQ in 1996, and 20 years since the Usenix paper (PDF) describing the Zephyr IM protocol that spread to MIT and Carnegie Mellon University. By now, encryption should be commonplace.
We found that only half of the services provide complete encryption: AOL Instant Messenger, Google Talk, IBM’s Lotus Sametime, and Skype do. To their credit, not one service says it keeps logs of the content of users’ communications (a certain lure for federal investigators or snoopy divorce attorneys). For connection logs, Microsoft alone said it keeps none at all–though Google and Skype said their logs were deleted after a short time.
Encryption is important. If you’re using an open wireless connection, anyone who downloads free software like dSniff can intercept unencrypted IM communications streams. WildPackets sells to police an EtherPeek plug-in it says can intercept and decode unencrypted IM conversations in wiretap situations (plus Web-based e-mail, VoIP calls, and so on).
All surveys have limitations, including ours. The fact that IM encryption is used is insufficient; it could always be a poor choice of an algorithm or there could be implementation errors that allow it to be bypassed in practice. Our survey will not be the final word in this area.
Jabber is worth a special note. While nearly all of our survey respondents use proprietary, closed systems, Jabber is based on open standards set by the Internet Engineering Task Force. Formally called XMPP, Jabber lets organizations run their own servers and tends to be more flexible.
Google adopted it for Google Talk, and other clients that support Jabber include Apple’s iChat, Adium (OS X), Trillian Pro (with a plug-in), and Psi. Jabber uses encryption both to log on and to protect conversations once a connection is established. We didn’t formally include it in our survey because anyone can set up their own Jabber server with their own configuration.
Facebook Chat is the least secure and privacy-protective of the lot. As far as we can determine, it fails to use encryption to protect logging in (thus passwords can be gleaned) and fails to secure the conversations, too. We’d like to tell you more about Facebook Chat, but the company sent us a one-line e-mail message saying it was refusing to answer the same questions that its competitors did with little fuss.
We intentionally left out Apple because its iChat software uses the AOL Instant Messenger network. Macintosh users who have purchased a .Mac membership can activate encryption for IM, audio and video chats, and file transfers.
| Secure logging-in | Secure conversations | Logs kept of user logins | Logs kept of message content | For how long | Government wiretapping | |
| AOL AIM | Yes | Yes | Yes | No | Won’t say | Won’t say |
| AOL ICQ | Yes | No | Yes | No | Won’t say | Won’t say |
| Facebook Chat[1] | No | No | Refused to answer | Refused to answer[2] | Refused to answer | Refused to answer |
| Google Talk | Yes | Yes[3] | Yes | No[4] | Four weeks | Won’t say |
| IBM Lotus Sametime | Yes | Yes | Yes | Configurable | Configurable | N/A |
| Microsoft’s Windows Live Messenger | Yes | No[5] | No | No | N/A | Won’t say |
| Skype | Yes | Yes | Yes | No | “A short time” | Cannot comply with wiretaps[6] |
| Yahoo Messenger | Yes | No | Yes | No | As long as “necessary” | Won’t say |
[1] Over the course of a week, Facebook refused to reply to questions.
[2] Facebook has said both that chat history “is not logged permanently” and that it is archived for 90 days.
[3] Encryption is on by default for the downloadable client, off by default for the Web, and not supported with the Google Talk Gadget.
[4] Configurable: users can choose to log conversations in their Gmail chat archives if they wish.
[5] Conversations are unencrypted, but files exchanged via Windows Live Messenger are encrypted.
[6] Skype was the only IM company that said it could not perform a live interception if presented with a wiretap request: “Because of Skype’s peer-to-peer architecture and encryption techniques, Skype would not be able to comply with such a request.”
Q: Does your service use encryption for authentication when users log on?
Yes
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
Yes
Q: Is encryption turned on or off by default?
On by default
Q: Does your service support the OTR (Off the Record) standard? If it uses non-OTR encryption, what kind?
No. AIM supports TLS. [Ed. Note: TLS, or Transport Layer Security, is the successor to Secure Sockets Layer. It supports a variety of cryptographic ciphers for scrambling the content of messages, including AES and Triple DES. It also provides methods for authentication.]
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address? If so, what information is stored?
Yes, we keep logs of connection information, such as sign on/off and IP address.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
No
Q: If any connection or content logs are stored, how long is each type kept?
Connection logs are retained according to the needs of the business for operational and quality control purposes and then regularly deleted.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
Yes
Q: If so, how many law enforcement requests have you received?
We do not share details about requests we receive from law enforcement.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
We do not share details about requests we receive from law enforcement.
Q: Does your service use encryption for authentication when users log on?
Yes
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
No. Message delivery encryption is under consideration for future product releases.
Q: Is encryption turned on or off by default?
N/A
Q: Does your service support the OTR standard? If it uses non-OTR encryption, what kind?
No
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address? If so, what information is stored?
Yes, we keep logs of connection information, such as sign on/off and IP address.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
No
Q: If any connection or content logs are stored, how long is each type kept?
Connection logs are retained according to the needs of the business for operational and quality control purposes and then regularly deleted.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
Yes
Q: If so, how many law enforcement requests have you received?
We do not share details about requests we receive from law enforcement.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
We do not share details about requests we receive from law enforcement.
Q: Does your service use encryption for authentication when users log on?
Yes.
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
Our download client uses encryption. Our Web client sends messages in plain text, but users can opt in to HTTPS if they want encryption. HTTPS does not currently work with the Google Talk Gadget.
Q: Is encryption turned on or off by default?
Encryption is turned on by default for the download client and off by default for the Web client.
Q: Does your service support the OTR standard? If it uses non-OTR encryption, what kind?
Google clients do not currently support OTR. We use TLS for XMPP client to server, and HTTPS for Web clients if users opt in. [Ed. Note: TLS, or Transport Layer Security, is the successor to Secure Sockets Layer. It supports a variety of cryptographic ciphers for scrambling the content of messages, including AES and Triple DES. It also provides methods for authentication.]
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address? If so, what information is stored?
The service logs standard data, including the IP address, user name, time stamp, and client type, but does not log chat content.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
Users may choose to chat “off the record’ in which case chats are not saved in their Gmail chat archives. If a user does not go “off the record,” then chat communications are saved and viewable to the participants of the chat within their Gmail account.
Q: If any connection or content logs are stored, how long is each type kept?
The service logs standard data (including the IP address, user name, time stamp, and client type), and stores this data for four weeks. Connection logs not tied to a Gmail account are kept for as long as they are useful. Users may choose to chat “off the record” in which case chats are not saved in their Gmail chat archives. If a user does not go “off the record” then chat communications are saved and viewable to the participants of the chat within their Gmail account.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
As a matter of policy, we do not comment on the nature or substance of law enforcement requests to Google. Whenever possible, we do our best to notify the subject named in such requests in order to give them the opportunity to object.
Q: If so, how many law enforcement requests have you received?
As a matter of policy, we do not share this information.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
As a matter of policy, we do not comment on the nature or substance of law enforcement requests to Google. Whenever possible, we do our best to notify the subject named in such requests in order to give them the opportunity to object.
[Ed. Note: IBM appended this explanation to its response: “Lotus Sametime is an enterprise on-premise unified communications solution. While IBM Global Technology Services offers managed hosting services for Lotus Sametime, it is typically sold as an on-premise solution. Answers below reflect Sametime as an on-premise solution. The answers would also apply for a hosted offering from IBM or IBM Business Partners.”]
Q: Does your service use encryption for authentication when users log on?
As enterprise-grade software, Lotus Sametime offers the security that businesses require. Lotus Sametime authentication gives businesses the confidence of knowing that the people they communicate with are who they say they are, while password protection helps ensure that only invited participants can attend Web conferences. By default, all authentication and authorization credentials are encrypted using 128-bit encryption. Lotus Sametime also supports compliance with FIPS-140, the U.S. Department of Defense standard.
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
Yes, Lotus Sametime software can encrypt presence, instant messages, Web conferences, VoIP voice chats, and point-to-point video conversa?tions to help businesses protect sensitive information. By default, Lotus Sametime uses 128-bit encryption, Lotus Sametime also supports compliance with FIPS-140, the U.S. Department of Defense standard.
Q: Is encryption turned on or off by default?
Encryption is turned on by default.
Q: Does your service support the OTR standard? If it uses non-OTR encryption, what kind?
Lotus Sametime does not support the OTR standard. By default Lotus Sametime uses 128-bit RC2 encryption. Lotus Sametime also supports compliance with FIPS-140, the U.S. Department of Defense standard.
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address?
Yes, Lotus Sametime provides a variety of logging options that are configurable by the system administrator. Through the Sametime Tool Kits, Sametime also integrates with a variety of third-party compliance software.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
The system administrator has the ability to configure these types of capabilities. This type of information can also be captured by third-party compliance software such as Facetime, Akonix, and Symantec.
Q: If any connection or content logs are stored, how long is each type kept?
Lotus Sametime provides the flexibility to keep the logs for as long as a business requires. The system administrator sets the duration of the storage of the logs based on the needs of the enterprise.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
This question does not apply to Sametime because it is not a service.
Q: If so, how many law enforcement requests have you received?
This question does not apply to Sametime because it is not a service.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
This question does not apply to Lotus Sametime because it is not a service.
Q: Does your service use encryption for authentication when users log on?
Windows Live Messenger accounts that are accessed upon authentication of a user’s Windows Live ID and password are protected by industry standard SSL encryption. [Ed. Note: SSL is Secure Sockets Layer, also known as Transport Layer Security.]
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
We do not provide encryption for instant messages at this time. However, if a customer chooses to send or receive messages that contain a file, like a document or photo, Windows Live Messenger protects those files with the industry standard SSL encryption.
Q: Is encryption turned on or off by default?
Encryption of file transfer functions automatically and cannot be turned off.
Q: Does your service support the OTR standard? If it uses non-OTR encryption, what kind?
Windows Live does not use the OTR standard. Windows Live Messenger accounts are protected by industry standard SSL encryption.
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address? If so, what information is stored?
Windows Live Messenger does not maintain server-based logs of connection information. Microsoft is committed to protecting the privacy of its customers and believes they deserve to have their personal data used only in ways described to them. Microsoft’s privacy policy informs our customers of the ways in which they can control the collection, use and disclosure of their personal information. More information is available on Microsoft’s privacy policy at: http://privacy.microsoft.com/en-us/default.aspx.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
Windows Live Messenger does not maintain server-based logs of the content of messages that our customers send or receive. Microsoft is committed to protecting the privacy of its customers and believes they deserve to have their personal data used only in ways described to them. Microsoft’s privacy policy informs our customers of the ways in which they can control the collection, use and disclosure of their personal information. More information is available on Microsoft’s privacy policy at: http://privacy.microsoft.com/en-us/default.aspx.
Q: If any connection or content logs are stored, how long is each type kept?
Not applicable.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
We do not comment on specific requests from the government. Microsoft is committed to protecting the privacy of our customers and complies with all applicable privacy laws. In particular, the Electronic Communications Privacy Act (“ECPA”) protects customer records and the communications of customers of online services. As set forth above, however, Microsoft does not maintain records about our customers’ use of the IM service and would have no information to provide in response to a request from law enforcement.
Q: If so, how many law enforcement requests have you received?
We do not disclose how many government requests we receive; in certain circumstances, we are not permitted by law to disclose that we have received a government order. However, we follow ECPA in responding to all requests.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
We do not comment on specific requests from the government, but in general, we provide the government with the contents of communications intercepted in real-time only pursuant to a court order.
Q: Does your service use encryption for authentication when users log on?
Yes.
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
Yes. Skype’s tight security model is integrally linked to its underlying peer-to-peer (P2P) architecture. As a result, Skype’s traffic cannot be intercepted and decoded while in transit. In short, Skype provides transport-layer security to ensure that message content traveling over Skype cannot be tapped or intercepted.
Q: Is encryption turned on or off by default?
Skype’s encryption is always on and cannot be turned off.
Q: Does your service support the OTR standard? If it uses non-OTR encryption, what kind?
No. Skype employs strong end-to-end encryption using 256-bit AES, which is then authenticated by PKI cryptography, to guarantee authenticity, secrecy, and integrity of communication over Skype.
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address? If so, what information is stored?
Where servers are used to facilitate the offering of a product such as SkypeOut, only username, version, and IP address are stored.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
No. Skype does not record any content from communications.
Q: If any connection or content logs are stored, how long is each type kept?
Connection logs are kept for only a short time.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
Yes. We co-operate with law enforcement agencies as much as is legally and technically possible.
Q: If so, how many law enforcement requests have you received?
That is confidential information.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
We have not received any subpoenas or court orders asking us to perform a live interception or wiretap of Skype-to-Skype communications. In any event, because of Skype’s peer-to-peer architecture and encryption techniques, Skype would not be able to comply with such a request.
Q: Does your service use encryption for authentication when users log on?
Yahoo Messenger for the Web and the current downloadable Yahoo Messenger uses SSL to protect the user’s password during authentication. [Ed. Note: SSL is Secure Sockets Layer, also known as Transport Layer Security.]
Q: Does your service use encryption for message delivery, meaning when your users send and receive messages?
Yahoo Messenger does not use encryption for message delivery.
Q: Is encryption turned on or off by default?
The encryption as described above in No. 1 is on by default.
Q: Does your service support the OTR standard? If it uses non-OTR encryption, what kind?
Yahoo Messenger does not use Off-the-Record cryptographic protocol. We use the Secure Sockets Layer (SSL) standard during password authentication as described in our answer to No. 1.
Q: Does your service keep server-based logs of connection information, such as when a particular user signs on or off and from what IP address? If so, what information is stored?
Yahoo logs Messenger activity consistent with Web-based services generally.
Q: Does your service keep server-based logs of the content of communications, meaning what a particular user sent and received?
Yahoo Messenger provides users with the ability to store and retrieve their IM messages. Users can choose not to use this convenient feature. Most versions of the downloadable Yahoo Messenger store conversations on the user’s computer while Yahoo Messenger for the Web stores these conversations on Yahoo servers.
Q: If any connection or content logs are stored, how long is each type kept?
Yahoo retains data as necessary to help comply with financial, legal, and security obligations, and for research purposes to improve our users’ experience with Messenger.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to turn over information about a user’s IM account?
Yahoo responds to law enforcement in compliance with all applicable laws.
Q: If so, how many law enforcement requests have you received?
Given the sensitive nature of this area and the potential negative impact on the investigative capabilities of public safety agencies, Yahoo does not discuss the details of law enforcement compliance. Yahoo responds to law enforcement in compliance with all applicable laws.
Q: Have you ever received a subpoena, court order or other law enforcement request asking you to perform a live interception or wiretap, meaning the contents of your users’ communications would be instantly forwarded to law enforcement?
Given the sensitive nature of this area and the potential negative impact on the investigative capabilities of public safety agencies, Yahoo does not discuss the details of law enforcement compliance. Yahoo responds to law enforcement in compliance with all applicable laws.
News.com’s Anne Broache contributed to this report

Declan McCullagh is the chief political correspondent for CNET. Declan previously was a reporter for Time and the Washington bureau chief for Wired and wrote the Taking Liberties section and Other People’s Money column for CBS News’ Web site.
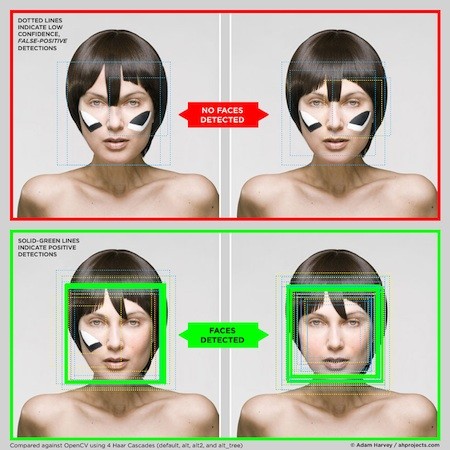
 Big Brother is watching you, though probably not in the ways most of us would imagine.
Big Brother is watching you, though probably not in the ways most of us would imagine.
Sure, the cameras at banks or airport checkpoints may be on the lookout for robbers or would-be terrorists, using facial recognition technology to match pictures to existing ones. But private enterprise is busy as well.
If you tag a picture of yourself on Facebook or Google’s Picasa, that image can be used to identify you in other pictures.
Adam Harvey says the technology is intruding on your right to privacy, and he’s figured out some low-tech ways to outsmart them.
“Don’t ask me about privacy, because I tend to talk too long about it,” he said. “When we live in an environment where we’re constantly being monitored, we cherish the right just to talk to someone face-to-face.”
Harvey, a New York web designer, started a project called CV Dazzle when he was getting his master’s degree at New York University in 2010. His objective: to show people how to hide in plain sight.
If you look at the images he generated, you’ll get a sense of what he has in mind. Face-recognition software looks for key points on one’s face, such as eyes, nose, and mouth, and where they meet and the distance between them. So he suggests simple ways to block them.
A spike of hair proved to be effective if it covered the area where the eyes, forehead and nose come together. Computer-vision software often looks for that spot, said Harvey, and will not detect a face without it.
Similarly, he said, a bit of face paint will confuse a computer. Harvey said he found that black geometric shapes, painted on one’s cheeks, would prevent a machine from registering that it was looking at a face.
Of course, these are not things that most people would do to their faces — but Harvey joked that in New York, where he lives, people with eccentric hairdos or makeup wouldn’t stand out much. And they’re more effective than hoodies or baseball caps pulled over one’s face. In those cases the software is unnecessary; people simply look as if they have something to hide.
Of course, the issue of privacy is complicated, especially when you’re talking about privacy in a public place. Richard Falkenrath, a principal with the Chertoff Group of security consultants who was an advisor on homeland security in the Bush administration, said facial recognition is not widely used in the United States except at places like security checkpoints. He looked at Adam Harvey’s work and said it would be most useful in social media, not as a way to get around government security.
“There are clearly certain activities for which you have no reasonable expectation of privacy,” Falkenrath said. “When you take out the garbage, people see you. When you walk down the street, people can take pictures of you.”
Would work like Harvey’s be helpful to criminals — the very people who ought not to be able to hide? Falkenrath said he didn’t think so, and Harvey said he did not intend it that way.
“This project is not about dodging the law, it’s about adapting to living in surveillance societies,” he said.
“In the next decade we’ll have to figure out how to balance security with privacy and move on,” Harvey said. “The research I’m doing is aimed at integrating fashion, privacy and technology to make real products that people can use.”
Late last year, president Obama signed a law that makes it possible to indefinitely detain terrorist suspects without any form of trial or due process. Peaceful protesters in Occupy movements all over the world have been labelled as terrorists by the authorities. Initiatives like SOPA promote diligent monitoring of communication channels. Thirty years ago, when Richard Stallman launched the GNU project, and during the three decades that followed, his sometimes extreme views and peculiar antics were ridiculed and disregarded as paranoia – but here we are, 2012, and his once paranoid what-ifs have become reality.
Up until relatively recently, it’s been easy to dismiss Richard Stallman as a paranoid fanatic, someone who lost touch with reality long ago. A sort of perpetual computer hippie, the perfect personification of the archetype of the unworldly basement-dwelling computer nerd. His beard, his hair, his outfits – in our visual world, it’s simply too easy to dismiss him.
His views have always been extreme. His only computer is a Lemote Yeelong netbook, because it’s the only computer which uses only Free software – no firmware blobs, no proprietary BIOS; it’s all Free. He also refuses to own a mobile phone, because they’re too easy to track; until there’s a mobile phone equivalent of the Yeelong, Stallman doesn’t want one. Generally, all software should be Free. Or, as the Free Software Foundation puts it:
I, too, disregarded Stallman as way too extreme. Free software to combat controlling and spying governments? Evil corporations out to take over the world? Software as a tool to monitor private communication channels? Right. Surely, Free and open source software is important, and I choose it whenever functional equivalence with proprietary solutions is reached, but that Stallman/FSF nonsense is way out there.
But here we are, at the start of 2012. Obama signed the NDAA for 2012, making it possible for American citizens to be detained indefinitely without any form of trial or due process, only because they are terrorist suspects. At the same time, we have SOPA, which, if passed, would enact a system in which websites can be taken off the web, again without any form of trial or due process, while also enabling the monitoring of internet traffic. Combine this with how the authorities labelled the Occupy movements – namely, as terrorists – and you can see where this is going.
In case all this reminds you of China and similarly totalitarian regimes, you’re not alone. Even the Motion Picture Association of America, the MPAA, proudly proclaims that what works for China, Syria, Iran, and others, should work for the US. China’s Great Firewall and similar filtering systems are glorified as workable solutions in what is supposed to be the free world.
The crux of the matter here is that unlike the days of yore, where repressive regimes needed elaborate networks of secret police and informants to monitor communication, all they need now is control over the software and hardware we use. Our desktops, laptops, tablets, smartphones, and all manner of devices play a role in virtually all of our communication. Think you’re in the clear when communicating face-to-face? Think again. How did you arrange the meet-up? Over the phone? The web? And what do you have in your pocket or bag, always connected to the network?
This is what Stallman has been warning us about all these years – and most of us, including myself, never really took him seriously. However, as the world changes, the importance of the ability to check what the code in your devices is doing – by someone else in case you lack the skills – becomes increasingly apparent. If we lose the ability to check what our own computers are doing, we’re boned.
That’s the very core of the Free Software Foundation’s and Stallman’s beliefs: that proprietary software takes control away from the user, which can lead to disastrous consequences, especially now that we rely on computers for virtually everything we do. The fact that Stallman foresaw this almost three decades ago is remarkable, and vindicates his activism. It justifies 30 years of Free Software Foundation.
And, in 2012, we’re probably going to need Free and open source software more than ever before. At the Chaos Computer Congress in Berlin late last year, Cory Doctorow held a presentation titled “The Coming War on General Purpose Computation“. In it, Doctorow warns that the general purpose computer, and more specifically, user control over general purpose computers, is perceived as a threat to the establishment. The copyright wars? Nothing but a prelude to the real war.
“As a member of the Walkman generation, I have made peace with the fact that I will require a hearing aid long before I die, and of course, it won’t be a hearing aid, it will be a computer I put in my body,” Doctorow explains, “So when I get into a car – a computer I put my body into – with my hearing aid – a computer I put inside my body – I want to know that these technologies are not designed to keep secrets from me, and to prevent me from terminating processes on them that work against my interests.”
And this is really the gist of it all. With computers taking care of things like hearing, driving, and more, we really can’t afford to be locked out of them. We need to be able to peek inside of them and see what they’re doing, to ensure we’re not being monitored, filtered, or whatever. Only a short while ago I would’ve declared this as pure paranoia – but with all that’s been going on recently, it’s no longer paranoia. It’s reality.
“Freedom in the future will require us to have the capacity to monitor our devices and set meaningful policy on them, to examine and terminate the processes that run on them, to maintain them as honest servants to our will, and not as traitors and spies working for criminals, thugs, and control freaks,” Doctorow warns, “And we haven’t lost yet, but we have to win the copyright wars to keep the Internet and the PC free and open. Because these are the materiel in the wars that are to come, we won’t be able to fight on without them.”
This is why you should support Android (not Google, but Android), even if you prefer the iPhone. This is why you should support Linux, even if you use Windows. This is why you should support Apache, even if you run IIS. There’s going to be a point where being Free/open is no longer a fun perk, but a necessity.
And that point is approaching fast.
SOURCE by Thom Holwerda on Mon 2nd Jan 2012 19:12 UTC


Dealing with police in the U.S. can be a touchy situation, no matter who you are, where you’re going, or what you’re up to. That’s why three law enforcement experts attending the 2011 Drug Policy Alliance conference in Los Angeles decided to stage a panel discussion about what people can do to prevent police encounters from becoming seriously detrimental to one’s life.
While the conversation was wide-ranging and covered a lengthy variety of topics, there were several main points they all made that can help every single person to deal with police in a manner that limits the potential for arrest or violence. (more…)
http://www.youtube.com/watch?v=1XFSAeLo65Q
Distributed denial of Service
the Barbs are Stacheldrat
When DOS attacks
Suits without a Head
Get scared and shit they Slacks
See what we lacks A Sense of Compassion
our Justice must be Swift
Hal Turner hurting the pockets
of White Supremacists
These Nemesises
Never This Vicious
We Troll the Net for Missions
If evils your position
Your files gonna come up Missing
http://www.youtube.com/watch?v=U8HRFBviUDs
Good evening, NATO.
We are Anonymous.
It has come to our attention that a NATO draft report has classified Anonymous a potential „threat to member states’ security”, and that you seek retaliation against us.
It is true that Anonymous has committed what you would call ‘cyber-attacks’ in protest against several military contractors, companies, lawmakers, and governments, and has continuously sought to fight against threats to our freedoms on the Internet. And since you consider state control of the Internet to be in the best interest of the various nations of your military alliance, you therefore consider us a potential threat to international security.
(more…)
http://www.youtube.com/watch?v=Q1A-DYK4M4Q
To the free-thinking citizens of the world:
Anonymous stands with the farmers and food organizations denouncing the practices of Monsanto We applaud the bravery of the organizations and citizens who are standing up to Monsanto, and we stand united with you against this oppressive corporate abuse. Monsanto is contaminating the world with chemicals and genetically modified food crops for profit while claiming to feed the hungry and protect the environment. Anonymous is everyone, Anyone who can not stand for injustice and decides to do something about it, We are all over the Earth and here to stay.
To Monsanto, we demand you STOP the following:
-Contaminating the global food chain with GMO’s.
– Intimidating small farmers with bullying and lawsuits.
– Propagating the use of destructive pesticides and herbicides across the globe.
– Using “Terminator Technology”, which renders plants sterile.
– Attempting to hijack UN climate change negotiations for your own fiscal benefit.
– Reducing farmland to desert through monoculture and the use of synthetic fertilizers.
-Inspiring suicides of hundreds of thousands of Indian farmers.
-Causing birth defects by continuing to produce the pesticide “Round-up”
-Attempting to bribe foriegn officials
-Infiltrating anti-GMO groups
(more…)


The act of keeping your identity hidden online by using connection methods and encryption methods, to make yourself untraceable to a person, website, company, school or whatever else you are doing/connecting to.