
Jan 26, 2012 | Black Technology
‘Time-travel from future to kill atom-smasher’ Hadron Collider to test for ‘God particle’ Scientists suggest God could be jinxing it In pictures: Tour the Large Hadron Collider In pictures: Tech conspiracy theories SCIENTISTS claim the giant...
Jan 26, 2012 | Activism, Black Technology
On return to Europe from the 2008 NEXUS Conference in Australia, flying out of Sydney, we stopped off in Thailand to visit a close friend who lives on the island of Koh Samui. Samui is well known as a travelers’ international crossroads, and is also a place...

Jan 26, 2012 | Black Technology
The world is changing fast–maybe faster than we ever thought. And within five years, science fiction is going to turn into non-fiction. We’ll be able to read each other’s minds, forget all our passwords, and create all our own homes’ energy....
Jan 26, 2012 | Black Technology, Video
RSA was hacked in March. This was one of the biggest hacks in history. The current theory is that a nation-state wanted to break into Lockheed-Martin and Northrop-Grumman to steal military secrets. They couldn’t do it, since these companies were using RSA...

Jan 26, 2012 | Black Technology
Speaking at the Chaos Computer Club (CCC) Congress in Berlin on Tuesday, a pair of researchers demonstrated a start-to-finish means of eavesdropping on encrypted GSM cellphone calls and text messages, using only four sub-$15 telephones as network “sniffers,” a laptop...
Jan 26, 2012 | Black Technology
Holographic disc storage may not have worked out so well for InPhase, but the folks at General Electric are still trying to make HVD work. Their latest breakthrough, shown off today at an IEEE symposium in Hawaii, is a new micro-holographic material which is 100x more...
Jan 26, 2012 | Black Technology
Share Tweet (NaturalNews) Even as the veggie blame game is now under way across the EU, where a super resistant strain of e.coli is sickening patients and filling hospitals in Germany, virtually no one is talking about how e.coli could have magically become resistant...

Jan 26, 2012 | Black Technology, Government Agenda
Following up on my story on the FBI’s computer-monitoring malware, the most interesting question unanswered in the FBI affidavit (.pdf) is how the bureau gets its “Computer and Internet Protocol Address Verifier” onto a target PC. In the Josh Glazebrook...
Jan 26, 2012 | Black Technology
Nuclear Engineer, Mehran Tavakoli Keshe, has came forward as being the developer of the technology being used in Iran’s new “flying saucer.” His technology is claimed to harness magnetism and gravity to allow travel throughout the solar system and beyond. On March...
Jan 26, 2012 | Black Technology, Government Agenda
Encryption, Warrants And The FBI Last Thursday, the House Judiciary Committee held a hearing focused on law enforcement surveillance of modern Internet services. Although both the New York Times and CNET have stories on the hearing, I don’t think either...
Jan 26, 2012 | Black Technology
One of the demands of the Egyptian revolution was to demolish one of the well-known security services for torture, grave human rights violations and spying on activists which is the State Security Investigations (SSI) and to have its officers set onto trials. Few...

Jan 26, 2012 | Black Technology
by Grazyna Fosar and Franz Bludorf Russian DNA Discoveries: Original version THE HUMAN DNA IS A BIOLOGICAL INTERNET and superior in many aspects to the artificial one. The latest Russian scientific research directly or indirectly explains phenomena such as...
Jan 26, 2012 | Black Technology
Date: Sat, 17 Sep 2011 20:37:56 -0500 From: Marsh Ray <marsh[at]extendedsubset.com> To: Discussion of cryptography and related <cryptography[at]randombit.net> Subject: [cryptography] Another data point on SSL “trusted” root CA reliability (S...
Jan 26, 2012 | Black Technology
JP Morgan is now able to run risk analysis and price its global credit portfolio in near real-time after implementing application-led, High Performance Computing (HPC) capabilities developed by Maxeler Technologies. The investment bank worked with HPC solutions...
Jan 26, 2012 | Black Technology
Crazy Computer I’m afraid. I’m afraid, Dave. Dave, my mind is going. I can feel it. I can feel it. My mind is going. There is no question about it. I can feel it. I can feel it. I can feel it. via Photobucket Researchers testing mental illness figured out...

Jan 26, 2012 | Black Technology
By Mac Slavo SHTFplan.com November 1st, 2011 While the FDA says growing your own food is against your best interests, consuming raw milk is dangerous, and alternative medicines need to be controlled by large pharmaceutical companies, subcutaneous passive...
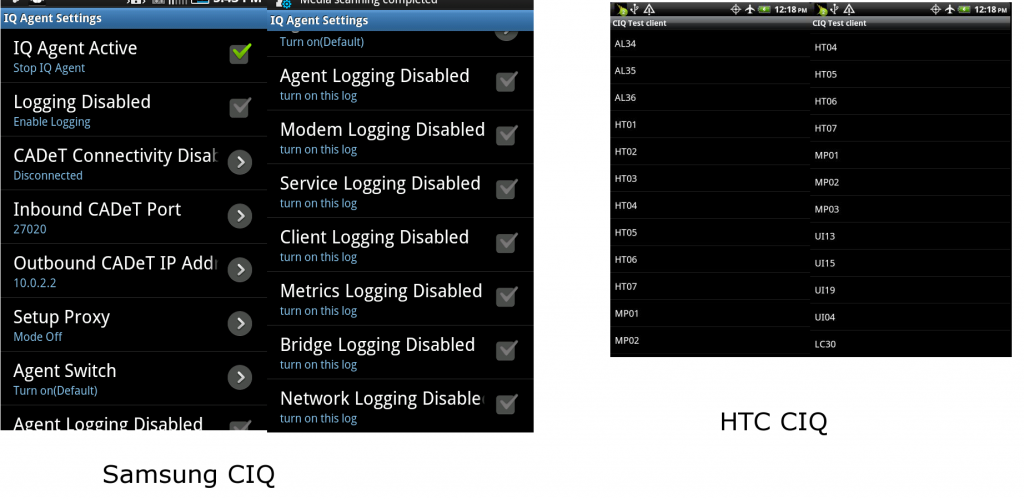
Jan 26, 2012 | Black Technology
CarrierIQ This information is written to the best of my knowledge using publicly available resources. No security was bypassed to obtain anything marked confidential, and Carrier IQ made no effort to protect said documents. You can take the Carrier IQ training...

Jan 26, 2012 | Black Technology
Brazilian police will use futuristic ‘Robocop-style’ glasses fitted with facial recognition equipment to identify and root out troublemakers at the 2014 World Cup. Military Police officials from Sao Paulo and Rio de Janeiro have been given demonstrations...

Jan 26, 2012 | Black Technology
On November 16, 2009, Greg Hoglund, a cofounder of computer security firm HBGary, sent an e-mail to two colleagues. The message came with an attachment, a Microsoft Word file called AL_QAEDA.doc, which had been further compressed and password protected for...
Jan 26, 2012 | Black Technology
A month ago I heard folks talking online about a virtual currency called bitcoin that is untraceable and un-hackable. Folks were using it to buy and sell drugs online, support content they liked and worst of all — gasp! — play poker.Bitcoin is a P2P...
Jan 26, 2012 | Black Technology
July 19th was a big day in hacker news. First, the Department of Justice announced the arrests of sixteen individuals thought to be associated with Anonymous and LulzSec, the loosely affiliated hacker groups that have been romping through corporate networks (and...
Jan 26, 2012 | Black Technology
All these pictures are from the book ‘ Microcosmos’, created by Brandon Brill from London. This book includes many scanning electron microscope (SEM) images of insects, human body parts and household items. These are the most amazing images of what is too...
Jan 26, 2012 | Black Technology, Video
...

Jan 26, 2012 | Anonymous, Black Technology
Hacked emails from security contractor HBGary Federal reveal a disturbing public-private partnership to spy on web users In February 2011, the hackers’ collective Anonymous released 70,000 emails from security contractor HBGary Federal, which revealed...

Jan 26, 2012 | Black Technology, Globalist Corporations
What corporate-driven “science” has in mind for the future of humanity is far different from the dreamy utopian landscape that’s been portrayed by the mainstream media. To hear the corporate-run media tell it, science is always “good” for humanity. Scientific...














