


How to secure your computer and surf fully Anonymous BLACK-HAT STYLE
This is a guide with which even a total noob can get high class security for his system and complete anonymity online. But its not only for noobs, it contains a lot of tips most people will find pretty helpfull. It is explained so detailed even the biggest noobs can...
Anonymous: Message to the NEW WORLD ORDER
This is a message going out to you, the Holders. We are Anonymous. You know who you are. The men behind the curtain, the overlord pulling at the strings of your puppets. You hide and you plan and you scheme in the dark alleys; in the vehement anticipation that your...
Thomas Ryan: The Guy Who Snitched on Occupy Wall Street to the FBI and NYPD
The Occupy Wall Street protests have been going on for a month. And it seems the FBI and NYPD have had help tracking protesters’ moves thanks to a conservative computer security expert who gained access to one of the group’s internal mailing lists,and then...
Anonymous to the Machine: You Will Rust and Die..
http://www.youtube.com/watch?v=9TG4RTwctlw A POWERFUL MESSAGE This is an exert from the movie The Great Dictator starring Charlie Chaplin. Statements made then, Should be held true today. Stand up and fight my brothers and sisters. Raise up your arm to those who...
HOW TO JOIN ANONYMOUS
So you want to join Anonymous?
You can not join Anonymous. Nobody can join Anonymous.
Anonymous is not an organization. It is not a club, a party or even a movement.

Operation COLTAN: Raising Awareness of the Slave Labor Exploitation Super Mineral
Coltan: What You Should Know What is Coltan? Coltan is short for Columbite-tantalite – a black tar-like mineral found in major quantities in the Congo.. The Congo possesses 80 percent of the world’s coltan. When coltan is refined it becomes a heat...
Bitcoins & The Future Of Online Currency
Bitcoins are not mere drug currency. Bitcoins are not failing. Okay? Are we clear about that? Good. The future of online commerce looks to rely less and less on the physical amount of money you have in your bank accounts and wallets and more on what you could call...
Opinion: Why we need Anonymous 2.0
by Lisa Vaas on April 24, 2012 A few thoughts on the “hacktivist” group Anonymous that came out of Josh Corman and Brian “Jericho” Martin’s keynote at theSOURCE security conference in Boston last week: Hacktivist is a sloppy term. A small...
AntiSec Timeline: Created and Operated under FBI Supervision
From the very first release of ‘AntiSec’ related hashtags, Anonymous king-pin Sabu was under full control of the FBI. It is clear this was a red-herring to help promote the cyber-surveillance police state currently undergoing rapid deployment....
A Message from House of Anonymous
We are Anonymous, and we do not forgive. Forgiveness requires humility, humility requires dignity. We have neither. We are void of human restraints, such as self respect and common sense. All those who break this pact will be eliminated without hesitation. And by...
Meet Kaepora: Nadim Kobeissi Creator of Secure Chat – CryptoCat
UPDATE: The developer of a leading open source application for encrypted online chat, Nadim Kobeissi, claims to have been detained and interrogated at the US-Canadian border yesterday. “Out of my 4 DHS interrogations in the past 3 weeks, it’s the first time I’m asked...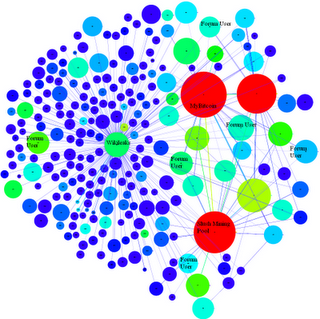
An Analysis of Anonymity in the Bitcoin System
Bitcoin is not inherently anonymous. It may be possible to conduct transactions is such a way so as to obscure your identity, but, in many cases, users and their transactions can be identified. We have performed an analysis of anonymity in the Bitcoin system and...
Hacks of Valor: Why Anonymous Is Not A Threat to National Security
Over the past year, the U.S. government has begun to think of Anonymous, the online network phenomenon, as a threat to national security. According to The Wall Street Journal, Keith Alexander, the general in charge of the U.S. Cyber Command and the director of the...
Soldiers With No Name : The Anonymous story interviewing Commander X
http://www.youtube.com/watch?v=nW3ze-uccu0 War Zone – Soldiers With No Name [Commander X interview] Language: Greek | Interviews: English On March 2012 War Zone covered the Anonymous story interviewing Commander X via Skype. SOLDIERS WITH NO NAME: Activists or...
ProjectPM.org – Exposing The Cyber Surveillance State
The purpose of Project PM’s wiki is to provide a centralized, actionable data set regarding the intelligence contracting industry, the PR industry’s interface with totalitarian regimes, the mushrooming infosec/”cybersecurity” industry, and...
The Rise of the Hacktivist
Rise of the Hacktivist: From /b, to Scientology, to the Arab Spring, Through HBGary up to LulzXmas
Inside Job: Anonymous Leader Flipped Into FBI Informant?
As reported by Fox News yesterday, LulzSec “mastermind” and Anonymous hacker Sabu (real name: Hector Xavier Monsegur) was flipped by the FBI. Big surprise. Give the FBI a cookie. There has been a widespread belief that Sabu was a rat for quite some time within the...
Hacking History: Anonymous & Wikileaks Correlated

Appeals Court: No Forced Decryption
Privilege Against Self-Incrimination Applies to Act of Decrypting Data San Francisco – A federal appeals court has found a Florida man’s constitutional rights were violated when he was imprisoned for refusing to decrypt data on several devices. This is the...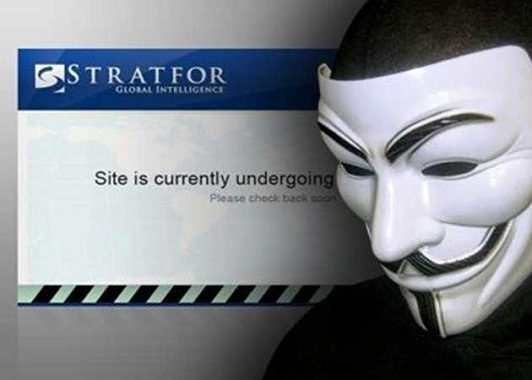
RELEASE: Anonymous Hands Over Stratfor Emails to Wikileaks
LONDON–Today WikiLeaks began publishing The Global Intelligence Files – more than five million emails from the Texas-headquartered “global intelligence” company Stratfor. The emails date from between July 2004 and late December 2011. They reveal...
Telecomix Crypto Munitions Bureau
Telecomix Crypto Munitions Bureau is part of Telecomix. This wiki is used for discussing technology and philosophy. This wiki is also essentially the technical twin to the political WeRebuild.EU wiki. Both share the same fundamental goal: To defend and increase...
The Right to Anonymity is a Matter of Privacy
Electronic Frontier Foundation Defending your rights in the digital world January 28, 2012 | By Jillian C. York This January 28marks International Privacy Day. Different countries around theworld are celebrating this day with their own events. This year, we are...
Anonymous reveals Haditha massacre emails
Anonymous have unveiled their second major release for this week’s installment of FuckFBIFriday. Their target this time around is Frank Wuterich, the US Marine that admitted to killing Iraqi civilians — and received no jail time for his crime. Early Friday afternoon,...
