
Nov 8, 2012 | Anonymous, Leaks
Paranoia is reputed to destroy you. But if you’re a whistleblower in search of a safe, neutral outlet, it just might save you instead. Par:AnoIA, short for Potentially Alarming Research: Anonymous Intelligence Agency, is a website designed to collect leaks, allow...

Nov 1, 2012 | Activism
Roughly 85,000 fewer people living in North America will be forced to drink and bathe in fluoridated water, thanks to four recent community victories preventing or overturning water fluoridation mandates. The towns of O’Fallon, Missouri; Rosetown, Saskatchewan;...

Oct 24, 2012 | Anonymous, Video
http://youtu.be/-_aWLu58Y1U New documentary We Are Legion puts an actual human face on Anonymous, the hacktivist group whose members usually are seen wearing Guy Fawkes masks — if they are seen at all. Considering Anonymous’ retaliatory acts against...
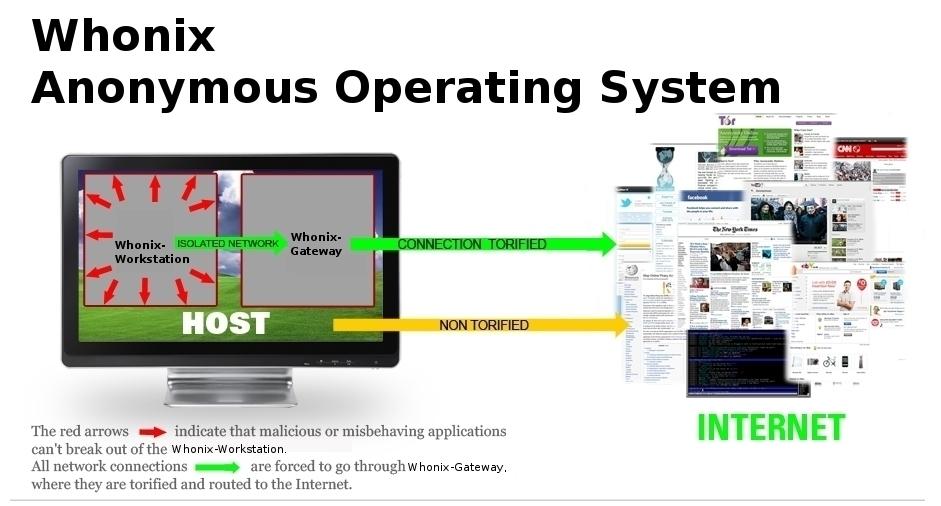
Oct 13, 2012 | Anonymous, Survivalism
Whonix is an anonymous general purpose operating system based on Virtual Box, Ubuntu GNU/Linux and Tor. By Whonix design, IP and DNS leaks are impossible. Not even malware with root rights can find out the user’s real IP/location. Whonix consists of two...

Oct 3, 2012 | Satire
Tupac Shakur, Bob Dylan, Lucille Ball, Jimmy Hendrix, Albert Einstein, John Lennon, Malcom X, Janice Joplin, Marylin Monroe, Martin Luther King

Oct 2, 2012 | Activism, News, WAR: By Design
Find Out If You Are Doing Things Which Might Be Considered Suspicious There have been so many anti-terrorism laws passed since 9/11 that it is hard to keep up on what kinds of things might get one on a “list” of suspected bad guys. We’ve prepared this quick checklist...

Oct 2, 2012 | Activism, Video
This is the official video for Lowkey’s single Tears to Laughter which has been supported by Palestine Solidarity Campaign, Stop the War Coalition, Viva Palestine and others. The song has been a huge hit amongst supporters of the Palestinian cause and Lowkey has...

Sep 28, 2012 | News
I don’t know about you, but I would label my personal knowledge of Hungary as wanting, if not painfully incomplete. It’s not an easy country to come to grips with, not least of all of course because Hungarian doesn’t look like any western language we...

Sep 28, 2012 | Activism
I will not idly stand by while law enforcement is administered only to the poor and disenfranchised while the rich flaunt their immunity. – Ray Lewis, Retired Philadelphia Police Captain, Arrested at Occupy Wallstreet Protest, NYC

Sep 27, 2012 | Activism, Video
Don’t be a Bystander. We have the power to effect change NOW – don’t be hypnotized by the false-reality and separation....

Sep 27, 2012 | Abuses of Power, Government Agenda, Video
While we in the civil liberties community disagree strongly with private investigator Steven Rambam’s admonition to “Get Over It,” after listening to him describe electronic surveillance powers it’s hard to disagree with the first part of the...

Sep 13, 2012 | Anonymous, News, Video
http://youtu.be/eky-q9CE_co For the second time this year, self-proclaimed Anonymous spokesman Barrett Brown was raided by the FBI. The latest dramatic incident occurred late Wednesday evening while Brown and another woman identified by some as his girlfriend were...

Sep 8, 2012 | Events & Assassinations, WAR: By Design
A clip from the documentary “Occupation 101”, a film which details the Israeli invasion and occupation of the Palestinian lands. If this story of Rachel Corrie, and activist killed while trying to prevent Palestinian homes from being demolished by...

Sep 5, 2012 | Anonymous, Video
You can Make a Difference. Everyone Has An Opportunity To Affect Change During this Crucial Time on Earth. ...

Aug 23, 2012 | Abuses of Power
Activists threaten legal action over failure to investigate Corporations in the UK who used a secret “blacklisting” database to screen out ‘left wing trouble-makers’ and union sympathizers as potential job recruits are facing renewed scrutiny after the...

Aug 17, 2012 | Abuses of Power, News
http://www.youtube.com/watch?v=UVWA_u6Uk_Q The Police, FBI and Secret Service swarmed in and took Brandon Raub to John Randolph Metal Hospital. This patriotic Marine had posted 5 posts on the Dont-Tread-On.Me blog linked below. Just glancing over them they seem to...

Aug 16, 2012 | Anonymous
For years Anonymous worked hard to protect our world and its peoples. NOW LISTEN CAREFULLY, This is an ALERT ABOUT SURVEILLANCE. Privacy of the people all over the world is suffering more and more outrages. We should not tolerate it. Cameras are everywhere even in our...

Aug 15, 2012 | Activism, Black Technology
http://youtu.be/3NHmOfwI1Kw Christopher Greene explains how thought crime will destroy the New World Order paradigm. GreeneWave is a completely independent alternative media channel focused on the economy and politics and dedicated to bringing controversial news and...

Aug 14, 2012 | Activism, Video
EFF activists Trevor Timm and Parker Higgins explain how widespread drones are becoming, how they’ve already been hacked, and how the situation may get a lot worse before it gets better. ...

Aug 6, 2012 | Activism, Government Agenda
Often, when folks find themselves having been visited or otherwise solicited for information by law enforcement, their reaction is to keep the fact that they’ve been targeted for government harassment quiet. In reality, however, the worst thing (next to...

Jul 15, 2012 | Anonymous
A Spanish researcher demos new satellite-hijacking tricks with cybercriminal potential. Satellites can bring a digital signal to places where the Internet seems like a miracle: off-the-grid desert solar farms, the Arctic or an aircraft carrier at sea. But in...

Jul 11, 2012 | Activism, Video
http://youtu.be/6wXkI4t7nuc An law school professor and former criminal defense attorney tells you why you should never agree to be interviewed by the police.

Jul 11, 2012 | Anonymous
VPNs and SSH tunnels can both securely “tunnel” network traffic over an encrypted connection. They’re similar in some ways, but different in others – if you’re trying to decide which to use, it helps to understand how each works. An SSH tunnel is often referred to as...

Jul 10, 2012 | Anonymous, Black Technology, Video
Ever wondered why your cell phone reception suddenly becomes terrible at protests? Ever worried that police could use electronic spoofing devices to suck up your mobile data because you are in the streets exercising your rights? You might have been onto something....

Jun 26, 2012 | Anonymous, Video
Protesting, Police Violence, Transparency, Global Government, all being manipulated against Humanity’s interests. 2012 is the year we take back our FREEDOMS. We do not forgive We do not forget We are legion Expect us ...


























