
Jul 19, 2015 | Enlightened Influences, Hollywood Programming
Matt Damon – “Things Are All Upside Down” Speech In this video actor Matt Damon speaks publicly on the New World Order and the Illuminati in a powerful speech. He mentions the “topsy turvy world”we’re living in where the wrong people are in jail and the wrong people...

Jul 15, 2015 | Black Technology, Leaks
One of the most widely used tools for Schools monitoring kids and restricting pupils’ internet use in UK schools has a serious security flaw which could leave hundreds of thousands of children’s personal information exposed to hackers, a researcher has warned. Impero...
Jun 25, 2015 | Globalist Corporations, News
A mere cursory glimpse into the future foretells of a world in which the Internet has been integrated into almost every facet of our lives. However, the flood of smartphones, laptops, and “Internet of Things”-enabled devices in recent years has led it to expand at a...

Apr 1, 2015 | Government Agenda, Nature Body Mind
When we shop for food in a supermarket or eat a fast food hamburger and fries, most of us don’t give much thought to the way the food was produced, or to the amount of suffering and environmental cost that went into each bite. But research is beginning to show...

Mar 19, 2015 | Anonymous, Whistleblowers & Dissidents
Anonymous radio host know as Lorax aka Adam Bennett Anon was arrested (full article). Everybody who has known Adam ‘Lorax’ Bennett aka Adam Bennett Anon knows he’s an awesome anon. Furthermore, the article now let us know he was also involved in his local...

Mar 13, 2015 | Anonymous, Whistleblowers & Dissidents
The case of Matt DeHart, a former U.S. drone pilot turned hacktivist, is as strange as it is disturbing. The 29-year-old was recently denied asylum in Canada, having fled there with his family after — he claims — he was drugged and tortured by agents of the FBI, who...

Mar 13, 2015 | Events & Assassinations, Whistleblowers & Dissidents
Aaron Swartz was a computer programmer and Internet activist who is often referred to as the third founder of Reddit. “”I don’t think I have any particular technical skills. I just got a really large head start.”” -Aaron Swartz Early Years Aaron...

Feb 25, 2015 | Black Technology, WAR: By Design
An unnamed scientific researcher walks out to her mailbox, shuffles through some bills and advertisements, and pulls out an envelope containing a CD of pictures from a recent scientific conference the researcher had attended in Houston. Excited – though maybe a bit...
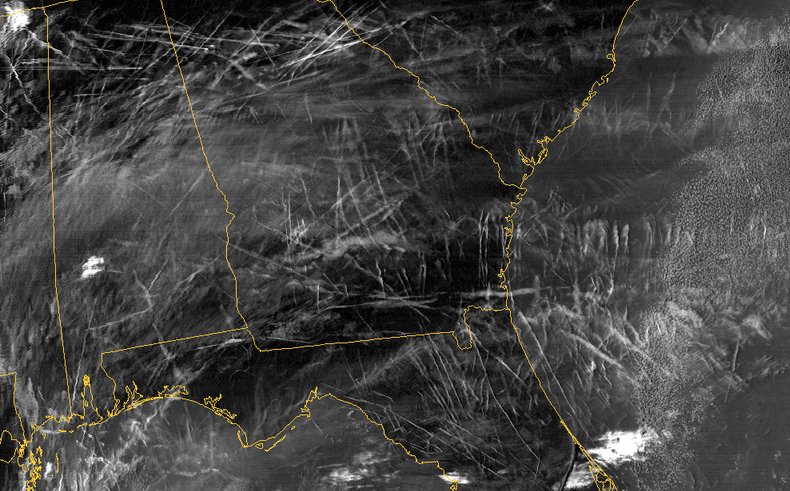
Feb 25, 2015 | Black Technology, Nature Body Mind
“Discoveries and inventions are not terminals; they are fresh starting points from which we can climb to new knowledge.” – Dr. Willis R. Whitney, founder of General Electric Laboratories After so many years of watching airplanes produce the lines in...

Feb 25, 2015 | Leaks, News
AMERICAN AND BRITISH Leaked: NSA Spies hacked into the internal computer network of the largest manufacturer of SIM cards in the world, stealing encryption keys used to protect the privacy of cellphone communications across the globe, according to top-secret documents...

Feb 25, 2015 | Enlightened Influences
Author and lecturer Stuart Wilde is one of the real characters of the self-help, human potential movement. His style is humorous, controversial, poignant and transformational. He has written over a dozen books, including those that make up the very successful Taos...

Feb 25, 2015 | Extra-Dimensional, Whistleblowers & Dissidents
Expert Consultant, Museum Curator, Investigator, UFOlogist Richard C. Hoagland is a former museum space science Curator; a former NASA Consultant; and, during the historic Apollo Missions to the Moon, was science advisor to Walter Cronkite and CBS News. In the...

Feb 25, 2015 | Activism, Enlightened Influences, Hollywood Programming
Oliver Stone, byname of William Oliver Stone (born September 15, 1946, New York, New York, U.S.), American film director, screenwriter, and producer known for his ambitious and often controversial movies. Stone, the son of a wealthy stockbroker, was raised in New...

Feb 25, 2015 | Extra-Dimensional, Whistleblowers & Dissidents
Philip Schneider was born April 23, 1947 and died (many assume murdered) in January 1996. Now Philip Schneider claimed to be an ex-government geologist and structural engineer who was involved in building underground military bases around the United States (possessing...

Feb 25, 2015 | 2020 Relevant, Activism, Whistleblowers & Dissidents
Doctor, Pastor, Human Rights Activist Born Michael Luther King, Jr., but later had his name changed to Martin Luther King Jr. His grandfather began the family’s long tenure as pastors of the Ebenezer Baptist Church in Atlanta, serving from 1914 to 1931; his...

Feb 25, 2015 | Government Agenda, Whistleblowers & Dissidents
Lawyer, Humanist, Activist Stanley Cohen Attorney affiliated with the Center for Constitutional Rights Has represented many radicals, revolutionaries, and Islamic extremists “If I don’t support the politics of political clients, I don’t take the case.” Views...

Feb 25, 2015 | Extra-Dimensional, Whistleblowers & Dissidents
Military Intelligence Officer, ET Contactee, Author, UFOlogist Bob Dean Robert O. Dean has been engaged in the field of UFO research for the last 40 years. He began this research on active duty in the US ARMY where he served for 27 years. He retired as Command...

Feb 16, 2015 | Government Agenda, Video
A pilot shots a chemical plane from his cockpit: the video shows an aircraft that spread chemtrails over Canada from the nozzles. The footage is the irrefutable proof of a chemical and clandestine operation that a bold pilot offers to the public in order to...
Feb 16, 2015 | Black Technology, News
There is often times a trade-off between security and convenience. With Home Hacks the more easily you can access your personal data, the easier someone else can too, making anything that you put online a potential target for hackers. A growing source of concern for...

Feb 13, 2015 | WAR: By Design
Israel’s “Smart” Weapons Kill Sabah Abu Jayab, known to her family and friends as Um Ahmad, walked through her home pointing out everything that had to be replaced after Israel’s 2014 assault on the besieged Gaza Strip. “This is all new,” Um Ahmad, a...

Feb 1, 2015 | Events & Assassinations, News
BREAKING: INFORMANT? Paris Terror Suspect on US Watch List Met With French President Sarkozy in 2009 21st Century Wire says… Charlie Hebdo As the dust settles from this week’s terror extravaganza in France, more loose ends are turning up (or being tied up), with this...

Jan 31, 2015 | News, WAR: By Design
Isreal is Getting Away with Murder On January 28th a barrage of Israeli artillery fire struck near the South Lebanese village of Ghajar, killing United Nations peacekeeper Francisco Javier Soria. Soria, 36, was a Spanish citizen deployed with the United Nations...

Jan 31, 2015 | Government Agenda, News
How to identify CIA The operations of secret intelligence agencies aiming at the manipulation of public opinion generally involve a combination of cynical deception with the pathetic gullibility of the targeted populations. There is ample reason to believe that the...

Jan 10, 2015 | Scientists Re-Booted
Robotics expert, NASA at the JPL. Alberto Behar Mr Behar died instantly when his single-engine plane nosedived shortly after takeoff Friday from Van Nuys Airport He worked on two Mars missions and spent years researching how robots work in harsh environments like...

Dec 17, 2014 | Events & Assassinations, Whistleblowers & Dissidents
Patrick Daniel “Pat” Tillman was an American football player who left his professional career and enlisted in the United States Army in June 2002 in the aftermath of the September 11 attacks. During his stay in Afghanistan, he quickly realized there was...


























