
Oct 24, 2014 | Enlightened Influences
Actor, Musician, Activist “It’s time for American citizens to stand up and pay attention to what we’re here for, and what this country was founded upon…and where it could be going if we, each one of us, does not stand up and write our...
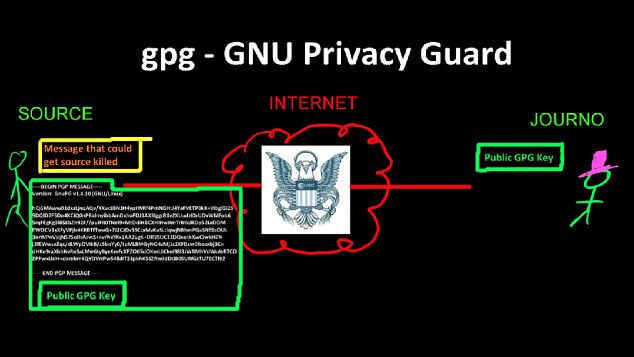
May 15, 2014 | Anonymous, Leaks, News, Video
Snowden made video to teach reporter how to speak with him securely It explains how to use Public Key Encryption to scramble online messages Privacy campaigners call on ordinary people to learn how to use the method +4 Whistleblower: The tutorial Edward Snowden made...

Oct 24, 2012 | News
United Nations report calls for Internet surveillance, saying lack of “internationally agreed framework for retention of data” is a problem, as are open Wi-Fi networks in airports, cafes, and libraries. The United Nations is calling for more surveillance...
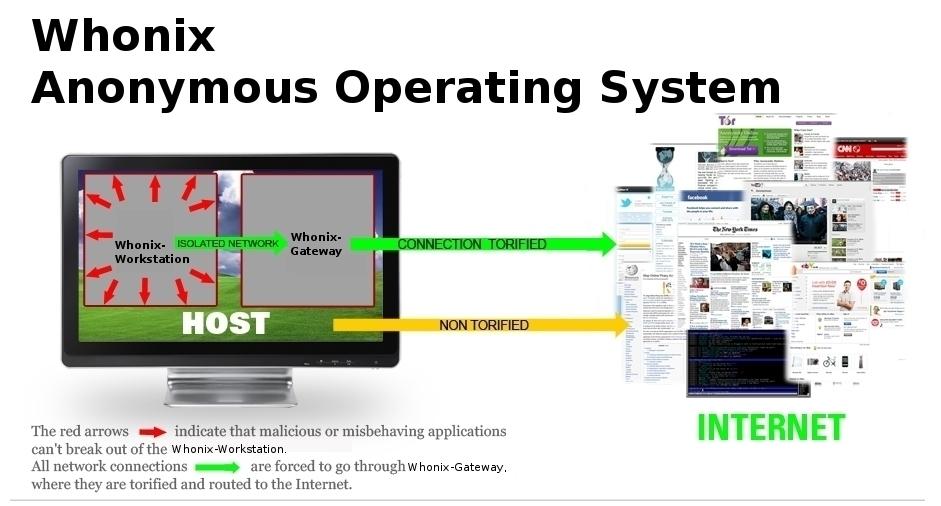
Oct 13, 2012 | Anonymous, Survivalism
Whonix is an anonymous general purpose operating system based on Virtual Box, Ubuntu GNU/Linux and Tor. By Whonix design, IP and DNS leaks are impossible. Not even malware with root rights can find out the user’s real IP/location. Whonix consists of two...

Oct 10, 2012 | Activism, News
The Supreme Court refused to hear a case on Tuesday that holds telecom companies accountable for letting the National Security Agency spy on unknowing Americans without a warrant. Dating back to 2006 when the American Civil Liberties Union and the Electronic Frontier...

Oct 2, 2012 | Activism, News, WAR: By Design
Find Out If You Are Doing Things Which Might Be Considered Suspicious There have been so many anti-terrorism laws passed since 9/11 that it is hard to keep up on what kinds of things might get one on a “list” of suspected bad guys. We’ve prepared this quick checklist...

Sep 28, 2012 | Black Technology, Government Agenda
You are looking at an insect spy drone for urban areas, already in production, funded by the US Government. It can be remotely controlled an is equipped with a Camera and Microphone. It can land on you and may have the potential to take a DNA sample, or leave...

Sep 28, 2012 | Activism, News
Indefinite detention, targeted killing and warrantless wiretapping are hot issues in the courts this week. Here’s the latest: INDEFINITE DETENTION // The National Defense Authorization Act (NDAA) of 2012 provision that allows the government to indefinitely...

Sep 27, 2012 | Abuses of Power, Activism
Smartphones can be a cop’s best friend. They are packed with private information like emails, text messages, photos, and calling history. Unsurprisingly, law enforcement agencies now routinely seize and search phones. This occurs at traffic stops, during raids...

Sep 27, 2012 | Abuses of Power, Government Agenda, Video
While we in the civil liberties community disagree strongly with private investigator Steven Rambam’s admonition to “Get Over It,” after listening to him describe electronic surveillance powers it’s hard to disagree with the first part of the...

Sep 25, 2012 | DCMX Radio
Topics of Discussion: Police State Build Up Surveillance Technology Life After Martial Law Elite Globalist Agenda Specific Solutions for Humanity Bob Tuskin An eternal student of economics, science and the arts. His radio career began at age 15, then with 911 as the...

Sep 7, 2012 | Government Agenda, News
The Next Generation Identification programme will include a nationwide database of criminal faces and other biometrics “FACE recognition is ‘now’,” declared Alessandro Acquisti of Carnegie Mellon University in Pittsburgh in a testimony before...

Sep 4, 2012 | Anonymous, News
Security professionals, geeks and hackers around the world are hosting a series of cryptography training sessions for the general public. The ‘crytoparty’ sessions were born in Australia and kicked off last week in Sydney and Canberra along with two in the...

Aug 23, 2012 | Black Technology, News
In 2008, a Reston, VA based corporation called Oceans’ Edge, Inc. applied for a patent. On March, 2012 the company’s application for an advanced mobile snooping technology suite was approved. The patent describes a Trojan-like program that can be secretly...

Aug 20, 2012 | Globalist Corporations, Video
In January 2012, two controversial pieces of legislation were making their way through the US Congress. SOPA, the Stop Online Piracy Act, and PIPA, the Protect Intellectual Property Act, were meant to crack down on the illegal sharing of digital media. The bills were...

Aug 16, 2012 | Anonymous
For years Anonymous worked hard to protect our world and its peoples. NOW LISTEN CAREFULLY, This is an ALERT ABOUT SURVEILLANCE. Privacy of the people all over the world is suffering more and more outrages. We should not tolerate it. Cameras are everywhere even in our...

Aug 14, 2012 | Black Technology, News, Video
The era of Big Data is upon us. Major corporations in the areas of advertising, social media, defense contracting, and computing are forming partnerships with government agencies to compile virtual dossiers on all humans. This data integration initiative is taking...

Aug 10, 2012 | Leaks, News
Former senior intelligence officials have created a detailed surveillance system more accurate than modern facial recognition technology — and have installed it across the US under the radar of most Americans, according to emails hacked by Anonymous. Every few...

Aug 9, 2012 | Activism, Globalist Corporations
Ok, I relent. Everyone wants to know why I left and answering individually isn’t scaling so here it is, laid out in its long form. Read a little (I get to the punch line in the 3rd paragraph) or read it all. But a warning in advance: there is no drama here, no...

Aug 3, 2012 | DCMX Radio
Cyber Security Industry Explosion, Intelligence Spying, Data-mining, Black-Hats, White-Hats, Gray-Hats abound. Alphabet Agencies, Corrupt Globalist Corporations exploiting your info. Micro Tutorial on Protecting Your Computer, Securing Your Internet Connection,...
Jul 23, 2012 | Black Technology, News
“If you’re concerned about it, maybe there’s a reason we should be flying over you, right?” said Douglas McDonald, the company’s director of special operations and president of a local chapter of the unmanned vehicle trade group....

Jul 15, 2012 | Anonymous
A Spanish researcher demos new satellite-hijacking tricks with cybercriminal potential. Satellites can bring a digital signal to places where the Internet seems like a miracle: off-the-grid desert solar farms, the Arctic or an aircraft carrier at sea. But in...

Jul 14, 2012 | Black Technology, News
Most of us don’t think much about it, but the truth is that people are being watched, tracked and monitored more today than at any other time in human history. The explosive growth of technology in recent years has given governments, spy agencies and big corporations...

Jul 12, 2012 | Abuses of Power, News
There was some surprise in the comments of yesterday’s post over the fact that the United Kingdom has effectively outlawed encryption: the UK will send its citizens to jail for up to five years if they cannot produce the key to an encrypted data set. First of all,...

Jul 11, 2012 | Black Technology, News
Within the next year or two, the U.S. Department of Homeland Security will instantly know everything about your body, clothes, and luggage with a new laser-based molecular scanner fired from 164 feet (50 meters) away. From traces of drugs or gun powder on your clothes...

























